Can you truly wield the power of your Raspberry Pi from any corner of the globe? The answer is a resounding yes! The humble Raspberry Pi, when correctly configured, transforms into a versatile digital Swiss Army knife, accessible and manageable regardless of your physical location. This capability unlocks a universe of possibilities, bridging the gap between personal tinkering and professional applications.
Whether you're a dedicated hobbyist crafting an intricate home automation system, a seasoned IT professional overseeing a distributed network of servers, or simply a curious individual seeking to expand your technical horizons, the ability to remotely access your Raspberry Pi is nothing short of revolutionary. This comprehensive guide serves as your roadmap, meticulously charting the course from initial setup to robust security measures and troubleshooting common pitfalls. Prepare to transform your Pi into a remotely accessible powerhouse, empowering you to control and monitor your projects with unprecedented freedom.
This article is a deep dive into the multifaceted world of Raspberry Pi remote access, offering a comprehensive exploration of various methodologies. We'll dissect the intricacies of SSH (Secure Shell), VNC (Virtual Network Computing), and other innovative approaches. By the time you finish reading, you'll possess a solid, practical understanding of how to securely and efficiently configure your Raspberry Pi for remote management, turning a simple device into a gateway to your digital world.
- Are Lindsey Graham Billy Graham Related Family Ties Explored
- Cory Weissmans Wife A Look Into Her Life Career
The very essence of remote access lies in its ability to grant you complete control over your Raspberry Pi from any location, provided you have a stable internet connection. This is particularly advantageous for projects demanding constant attention, regular software updates, or continuous data monitoring, eliminating the need for physical presence and the constraints of location. Imagine the freedom of being able to tinker, adjust, and monitor your projects from anywhere that's the power of remote access.
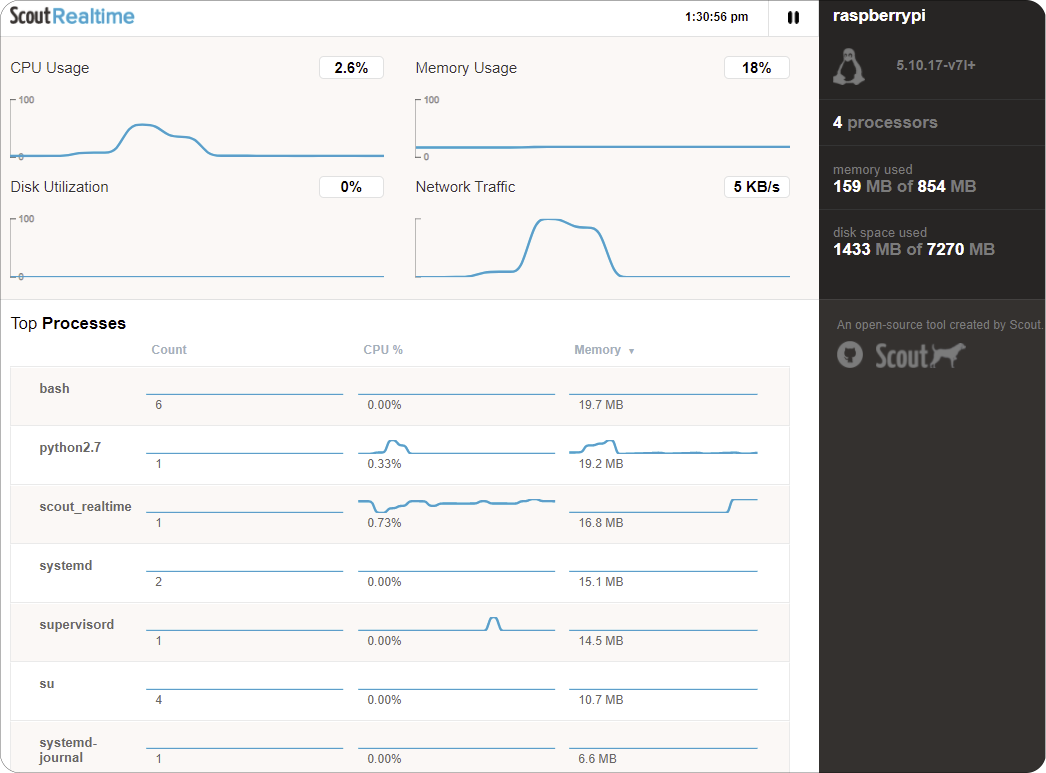
The process of accessing your Raspberry Pi remotely involves several key steps, each crucial to the overall success of the operation. These include the meticulous configuration of network settings, the enabling of specific communication protocols, and the stringent implementation of robust security measures. This detailed guide provides a comprehensive overview of the available tools and methods, ensuring a smooth, secure, and ultimately rewarding remote access experience.
Setting Up Your Raspberry Pi
Before embarking on the journey of remote access, it's paramount to ensure that your Raspberry Pi is properly configured and ready for the task. This preliminary stage involves installing the latest version of Raspberry Pi OS, the operating system that breathes life into your device, and setting up essential configurations, such as establishing a Wi-Fi connection and assigning a static IP address.
- Breaking Lisa Desjardins Illness A Health Update Amp Her Journey
- Kid Mom Cctv Heartwarming Moments Privacy In Public
- Install Raspberry Pi OS on your microSD card. This crucial step provides the foundation for all subsequent operations. Always download the latest version of the OS from the official Raspberry Pi website. This ensures optimal performance, incorporates the latest security patches, and provides the most stable environment for your projects.
- Connect your Raspberry Pi to your local network, using either a reliable Ethernet cable or a convenient Wi-Fi connection. A stable and consistent network connection is the cornerstone of successful remote access. Ensure that your network connection is robust and that your Pi can reliably communicate with the outside world.
- Assign a static IP address to your Raspberry Pi. This seemingly small step is profoundly important. A static IP address ensures that your Raspberry Pi's IP address remains constant, regardless of network fluctuations. This predictability makes it significantly easier to connect remotely because you won't have to constantly hunt for the device's current address.
Enabling SSH and VNC
SSH (Secure Shell) and VNC (Virtual Network Computing) are the two primary pathways most frequently used to access your Raspberry Pi remotely. Each method requires a degree of initial configuration on your Raspberry Pi, establishing the foundation for remote communication. Understanding these initial configurations is critical to establishing a secure and accessible connection.
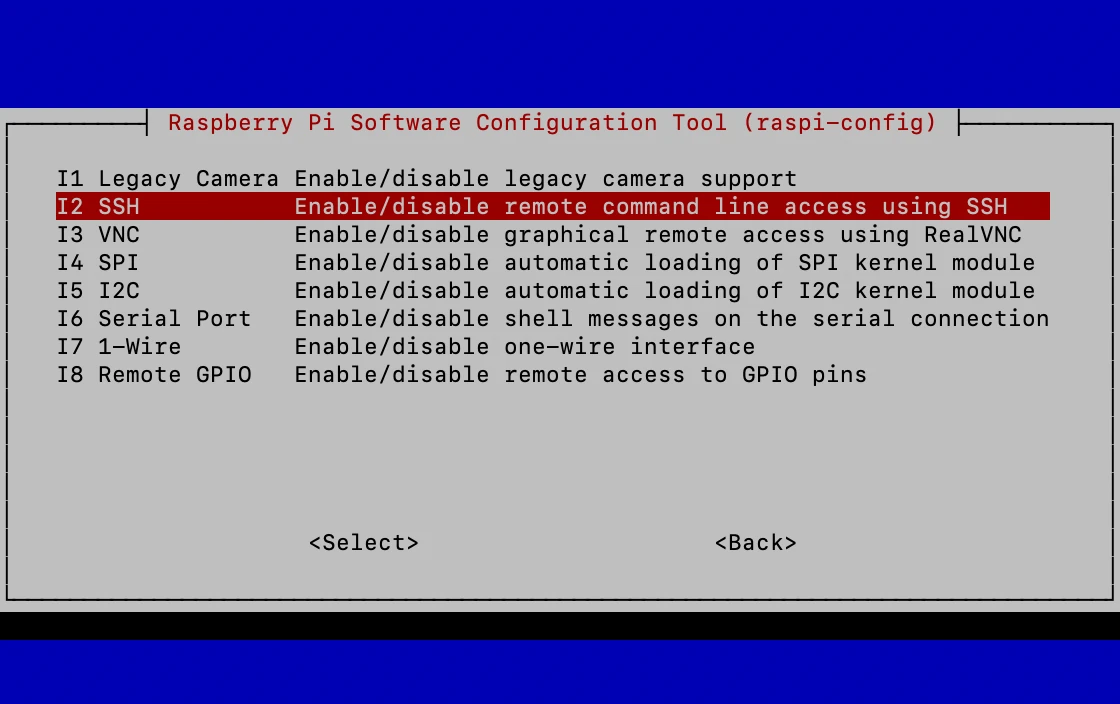
- Enable SSH by running the command `sudo raspi-config` in your terminal. This versatile tool gives you granular control over your Pi's settings. Navigate through the menu to "Interface Options" and then select the "SSH" option. Enable SSH to grant remote access via the command line. This enables you to input commands from afar.
- Install and configure a VNC Server for graphical access. VNC allows you to see and interact with your Raspberry Pi's desktop environment remotely. Its as if youre sitting right in front of your Pi, even when you're miles away. This is often preferred by users who want a more visual, hands-on experience with their Pi.
Accessing Raspberry Pi via SSH
SSH, or Secure Shell, is a secure protocol specifically designed to provide remote access to the command-line interface of your Raspberry Pi. It's a text-based interface, allowing you to execute commands, manage files, and control your system from a distance. This method is particularly favored by those who are comfortable working within a terminal environment, where efficiency and precise control are paramount.
Connecting via SSH
Establishing a connection to your Raspberry Pi via SSH is a straightforward process. By following these simple steps, you can unlock the power of remote command-line access.
- Ensure SSH is enabled on your Raspberry Pi. Before you begin, double-check that SSH is activated in the Raspberry Pi's configuration. This confirms that your Pi is listening for incoming SSH connections.
- Utilize an SSH client on your computer. A wide array of SSH clients are available for various operating systems. Popular choices include PuTTY, a reliable and widely-used client for Windows, and the built-in Terminal application, readily available on macOS and Linux systems.
- Enter the IP address of your Raspberry Pi when prompted by your SSH client. This vital step initiates the connection process. After entering the IP address, the client will attempt to connect to your Pi. You will then be prompted to provide your username and password to verify your identity, ensuring only authorized users gain access.
Securing SSH Connections
Security is paramount when remotely accessing your Raspberry Pi. Implementing these essential best practices significantly minimizes the risk of unauthorized access, protecting your device and your data. Vigilance in security is not merely a recommendation; it's an absolute necessity.
- Change the default SSH port (22) to a custom port. This seemingly simple step is an effective deterrent against automated attacks that scan for the standard port. Choose a port number outside the common range. A slightly more obscure port makes it more difficult for automated tools to find and exploit your SSH connection.
- Use strong passwords or SSH keys for authentication. Weak passwords are an open invitation to malicious actors. Opt for complex, unique passwords or, preferably, SSH keys. SSH keys provide a far more secure method of authentication as theyre significantly harder to compromise than a simple password. Generating a key pair, placing the public key on your Raspberry Pi, and configuring SSH to use key-based authentication eliminates the need to enter a password, adding a crucial layer of protection.
- Disable root login to prevent unauthorized access. Disabling direct root login adds an additional layer of security. Instead, create a standard user account with sudo privileges and use that for remote access. This best practice reduces the risk of a compromised root account.
Using VNC for Remote Access
VNC, or Virtual Network Computing, provides a graphical interface for remote access to your Raspberry Pi. This allows you to interact with your Pi's desktop environment as if you were sitting in front of it, making it an excellent choice for individuals who prefer a more visual, hands-on approach to remote control. The following is a step-by-step guide to setting up and using VNC effectively, ensuring a seamless and intuitive remote access experience.
Installing VNC Server
To utilize VNC for remote access, you must first install a VNC Server on your Raspberry Pi. This server acts as the bridge, allowing your client machine to connect to and control the graphical desktop. Here's the streamlined process:
- Update and upgrade the package list by running `sudo apt update` followed by `sudo apt install realvnc-vnc-server realvnc-vnc-viewer`. This crucial step ensures you have the latest package information and installs both the VNC server and the corresponding viewer. This update makes the installation process smoother and ensures that you benefit from any performance and security updates.
- Enable VNC through the Raspberry Pi Configuration tool. Open the tool using `sudo raspi-config`, navigate to "Interface Options," and then enable VNC. This action allows the VNC server to start automatically when your Pi boots, ensuring immediate accessibility.
Connecting with a VNC Client
Once the VNC Server is successfully installed on your Raspberry Pi, you can establish a connection using a VNC client, bridging the gap between your device and your remote control. Follow these instructions to establish a reliable connection and begin enjoying the benefits of remote access.
- Download and install a VNC client on your computer. Several VNC clients are available across various platforms. Some popular options include RealVNC Viewer (which is cross-platform), TightVNC, and others. Select the client thats compatible with your specific operating system.
- Enter the IP address of your Raspberry Pi when prompted by the VNC client. Ensure that you also include the display number (usually :1) after the IP address; for example, `192.168.1.100:1`. This tells the client which display on your Pi to connect to.
- Log in using your Raspberry Pi credentials. You will need to enter your username and password to access the graphical desktop environment. This authentication step ensures that only authorized users gain access to your Pi's desktop.
Network Configuration for Remote Access
Properly configuring your network is a fundamental requirement for achieving successful remote access. This section will explore the essential aspects of network configuration, including the often-overlooked details of port forwarding and the advantages of implementing dynamic DNS. Understanding these elements is crucial for establishing a reliable and secure remote connection.
Port Forwarding
Port forwarding is a critical step in allowing external devices to access your Raspberry Pi through your router. This allows devices outside your local network to "see" your Pi. It acts as a virtual pathway, guiding incoming traffic to the correct device. Follow these steps to configure it:
- Log in to your router's admin interface. This typically involves entering the router's IP address in your web browser and logging in with your administrator credentials. This is the gateway to your network settings. If you do not know your routers IP address, it's usually provided in your router's documentation or by your internet service provider.
- Set up port forwarding for the SSH (port 22, or your custom port) and VNC (port 5900, or the appropriate port) ports. You will need to specify the internal IP address of your Raspberry Pi and the port numbers. This action tells your router to direct incoming traffic on these specific ports to your Raspberry Pi, effectively making it accessible from the outside world.
Dynamic DNS
Dynamic DNS (DDNS) services play a crucial role by providing a persistent hostname for your Raspberry Pi, even when your public IP address changes. This ensures that you can always find your Pi, regardless of IP address fluctuations. This becomes particularly important for those who rely on remote access for consistent and reliable connectivity. Consider utilizing services like No-IP or DuckDNS to ensure that you can consistently access your Raspberry Pi.
| Category | Details |
|---|---|
| Name | Raspberry Pi Remote Access |
| Description | A comprehensive guide on configuring a Raspberry Pi for remote access, including SSH, VNC, port forwarding, and security measures. |
| Primary Functionality | Enables users to control and manage a Raspberry Pi from anywhere with an internet connection. |
| Key Features |
|
| Target Audience | Tech enthusiasts, home automation builders, remote server managers, and anyone looking to control a Raspberry Pi remotely. |
| Benefits |
|
| Required Components |
|
| Security Considerations |
|
| Tools and Software |
|
| Additional Tips |
|
| Reference | Official Raspberry Pi Documentation |
Ensuring Security for Remote Connections
Security is paramount when enabling remote access to your Raspberry Pi. Failing to secure your device can expose it to a range of vulnerabilities, potentially leading to data breaches and unwanted access. This section focuses on outlining and implementing the essential best practices necessary to protect your device from unauthorized access and mitigate potential threats, ensuring a secure and protected remote access experience.
Firewall Configuration
Configuring a firewall is a critical first step in restricting access to only the essential ports, minimizing the attack surface. A well-configured firewall prevents unauthorized access to your device. The Uncomplicated Firewall (UFW) is a user-friendly and powerful option for this task:
- Use `sudo ufw allow 22` (or the custom port you chose) to allow SSH traffic. This command specifically permits incoming connections on the SSH port, allowing you to maintain remote command-line access. This ensures that your authorized connections can get through while blocking others.
- Block all other unnecessary ports. Closing off ports that aren't needed minimizes the potential attack surface and protects your Raspberry Pi from unwanted intrusion. You can block these ports by using the command `sudo ufw deny [port_number]`. This is a proactive step in reducing the risk of unauthorized access.
Regular Updates
Keeping your Raspberry Pi OS and all installed software up to date is an indispensable element in patching security vulnerabilities. These vulnerabilities can be exploited by malicious actors, allowing them to gain unauthorized access to your system. Regular updates are, therefore, a fundamental security practice. This ensures that your system is protected against known threats.
- Run `sudo apt update` to update the package lists. This command fetches the latest information about available packages from the software repositories. This informs your system about any new available versions and helps in keeping your system current.
- Run `sudo apt upgrade` to install the latest available updates. This command installs any available updates for the software on your Raspberry Pi. By regularly updating your system, you proactively defend against security vulnerabilities.
Tools and Software for Remote Access
Several tools and software solutions can significantly enhance your remote access experience, making it more efficient and user-friendly. Understanding the available options empowers you to choose the best tools for your needs, improving your remote access capabilities.
Third-Party Remote Access Tools
Consider leveraging third-party tools for streamlined remote access, offering an intuitive user interface and simplified setup. These tools often require minimal configuration, allowing you to quickly establish a remote connection.
- TeamViewer offers a user-friendly experience with both free and paid options for remote access. It provides cross-platform support and an easy setup process, making it an attractive choice for users of all skill levels.
- AnyDesk provides fast and reliable connections with minimal configuration. Known for its impressive performance and ease of use, AnyDesk is an excellent alternative to TeamViewer. It offers a simple interface that makes it simple to connect and control your Raspberry Pi.
Troubleshooting Common Issues
Encountering issues during remote access is a common occurrence. Troubleshooting these problems can be frustrating, but its essential to identify and resolve these challenges to ensure that your setup works seamlessly. This section provides practical solutions to overcome common issues, making it easier to regain control of your device.
Connection Issues
If you encounter difficulties connecting to your Raspberry Pi remotely, follow these steps to troubleshoot the problem methodically. A methodical approach to troubleshooting often leads to a faster resolution, getting you back to using your device remotely.
- Ensure your Raspberry Pi is connected to the network. First and foremost, verify the physical connection. Check the Ethernet cable (if applicable) or the Wi-Fi connection status. Ensuring the fundamental network connection is functioning is always the first step.
- Double-check the IP address and port settings. The IP address of your Raspberry Pi and the port number (22 for SSH, 5900 for VNC, or any custom port you may have configured) must be correct. Also, confirm that the port forwarding rules are set up correctly on your router. These settings must align for a successful connection.
Advanced Techniques for Remote Access
For more advanced users, this section dives into more complex methods for remote access, exploring techniques like using a reverse SSH tunnel or setting up a VPN (Virtual Private Network). These techniques allow for greater control and flexibility and can be critical when dealing with complex network configurations.
Reverse SSH Tunnel
A reverse SSH tunnel is a powerful technique that enables you to access your Raspberry Pi even if it's behind a firewall or a network where inbound connections are restricted. This is especially useful when your Raspberry Pi is situated on a private network or behind a router that doesn't permit direct inbound connections from the outside world.
- Run the command `ssh -R 2222:localhost:22 user@remote-server` to set up the tunnel. This command, executed from the Raspberry Pi itself, creates a secure connection to a remote server that you control. The `-R` option specifies that a remote port will be forwarded to the Raspberry Pi's local port. In this example, port 2222 on the remote server will be forwarded to port 22 (SSH) on your Raspberry Pi. You'll need to replace `user@remote-server` with the username and IP address or hostname of your remote server.
- Connect to your Raspberry Pi through the remote server. Once the tunnel is established, you can connect to your Raspberry Pi using the remote server's public IP address or hostname and the port number you specified for the tunnel (in this example, 2222). This effectively "bounces" the connection through the remote server to your Raspberry Pi.
Example: Let's say your Raspberry Pi's internal IP address is 192.168.1.100, and you've set up the reverse SSH tunnel as described above. If the remote server's public IP is 123.45.67.890, you would connect to your Raspberry Pi from your client machine using `ssh user@123.45.67.890 -p 2222`. The connection will be securely tunneled through the remote server.
The reverse SSH tunnel is a versatile and highly useful method for accessing devices behind firewalls or NAT (Network Address Translation) setups, as it initiates the connection from the Raspberry Pi itself, allowing for seamless remote access even when direct inbound connections are blocked by the networks security. This technique provides a vital workaround in situations where typical remote access methods are impractical.
By mastering these techniques, you can significantly enhance your ability to manage and control your Raspberry Pi from anywhere in the world, making it a truly flexible and accessible tool.
- Movierulz Hd Kannada Risks Alternatives Safe Streaming Guide
- Perdita Weeks A Beacon Of Hope Resilience Amidst Disability Challenges