Is securing your Internet of Things (IoT) devices a pressing concern? Mastering Secure Shell (SSH) for remote access to devices like the Raspberry Pi is not just a prudent choice; it's a fundamental necessity in today's interconnected world. The capacity to remotely manage and monitor your IoT setup from the convenience of your Windows machine has evolved from a luxury into an indispensable requirement. This comprehensive guide delves into the intricacies of configuring and utilizing SSH for your Raspberry Pi, ensuring a secure and efficient remote management experience.
The ability to remotely manage IoT devices is a critical skill, essential for both enthusiastic hobbyists and seasoned professional developers. SSH empowers you to securely connect to your Raspberry Pi from any Windows machine. This allows you to manage files, execute commands, and observe your IoT setup without requiring physical access to the device. This guide will equip you with the necessary knowledge and tools to successfully implement and use SSH for your Raspberry Pi projects.
Let's explore the advantages of utilizing SSH for your Raspberry Pi projects, providing a secure and efficient remote management experience. Below is a table of contents outlining the topics we'll cover:
- Merritt Wever Jonathan Majors The Untold Story Of Their Romance
- Understanding Maal49 Unveiling The Future Of Tech Innovation
SSH (Secure Shell) is a fundamental network protocol, providing encrypted communication between two devices. In the context of IoT devices such as the Raspberry Pi, SSH is an indispensable tool. It allows you to remotely control your Raspberry Pi from a Windows computer, ensuring secure and efficient operations.
Given the increasing prevalence of IoT devices, the demand for secure remote access solutions has grown exponentially. The Raspberry Pi, celebrated for its versatility and affordability as a single-board computer, is a cornerstone of countless IoT projects. By configuring SSH on your Raspberry Pi, you essentially unlock its full potential, freeing it from the limitations of physical proximity.
Why Choose SSH for IoT Devices?
- Encryption guarantees secure communication.
- Supports file transfers via SCP (Secure Copy Protocol).
- Compatible with a broad spectrum of operating systems and devices.
- Easy to set up and use, making it suitable for both beginners and experts.
Benefits of Using SSH for Raspberry Pi
Utilizing SSH with your Raspberry Pi unlocks a multitude of advantages, particularly relevant for IoT projects. Here are some key benefits:
- Remote Access: You can manage your Raspberry Pi from virtually anywhere in the world, provided you have an internet connection. This flexibility is invaluable for troubleshooting, making modifications, or monitoring your projects without needing to be physically present.
- Security: SSH encrypts all data transmitted between devices, providing a robust defense against potential eavesdropping and protecting sensitive information from unauthorized access. This is particularly crucial when dealing with IoT devices that might handle sensitive data or control critical systems.
- Efficiency: By running commands directly on the Raspberry Pi via SSH, you can streamline your workflow and achieve faster task completion. This eliminates the need to physically interact with the device for every command, saving time and improving overall productivity. The ability to automate tasks via SSH scripts further enhances efficiency.
- Cost-Effective: SSH eliminates the need for additional hardware or expensive software licenses. The software is generally free of charge.
These advantages make SSH an ideal choice for anyone venturing into IoT devices, whether for personal projects or large-scale enterprise applications. The ability to remotely control, monitor, and manage devices securely is a game-changer in the ever-expanding landscape of the Internet of Things.
System Requirements for SSH Setup
Before initiating the setup process, it's crucial to ensure you meet the following requirements. Successful implementation hinges on the compatibility of your hardware and software.
Raspberry Pi Requirements
- A Raspberry Pi (any model with SSH support) is the core of your remote access setup. Choose a model based on your project's requirements, considering factors such as processing power, memory, and connectivity options.
- Raspberry Pi OS or any other Linux-based operating system installed on the Raspberry Pi. The operating system provides the foundation for running SSH and other essential software. Ensure your chosen OS is up-to-date for optimal security and performance.
- An active internet connection for the Raspberry Pi is essential. This can be achieved through Ethernet or Wi-Fi. The Raspberry Pi needs a stable internet connection to communicate with your Windows machine.
Windows Requirements
- Windows 10 or later (note that the SSH client is built-in to Windows 10). The built-in SSH client simplifies the connection process.
- Administrator privileges are necessary for installing software, if necessary. These privileges allow you to make system-level changes required for software installation and configuration.
- An active internet connection for your Windows machine is also required. This connection enables communication with your Raspberry Pi over the network.
Meeting these requirements will facilitate a smooth setup process and help ensure optimal performance. Proper configuration is critical for a secure and reliable remote access connection.
How to Install SSH on Raspberry Pi
Installing SSH on your Raspberry Pi is a relatively straightforward process. Here's a detailed walkthrough to guide you through the setup.
Step 1
SSH is disabled by default on Raspberry Pi OS to enhance security. You'll need to enable it to proceed.
- Boot your Raspberry Pi and log in to its desktop environment or access it via a terminal connected to the device.
- Open the terminal (command line interface) and type
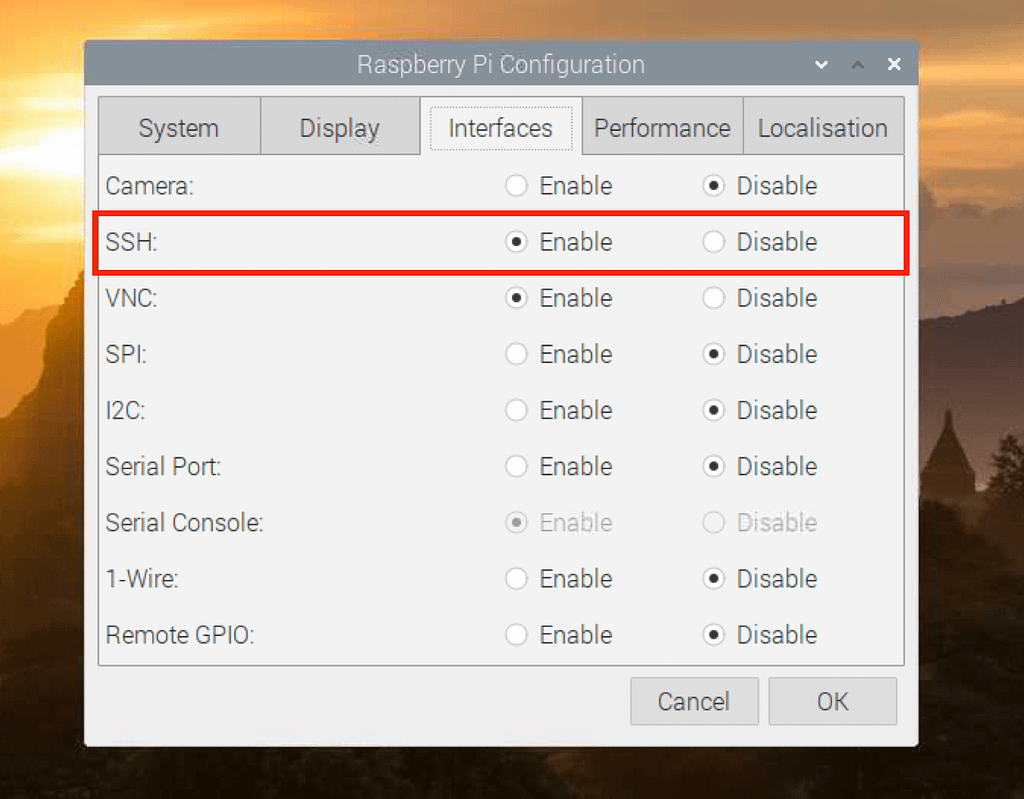
sudo raspi-configand press Enter. This command opens the Raspberry Pi configuration tool. - Select "Interfacing Options" using the arrow keys and then press Enter. This section controls the configuration of various hardware interfaces.
- Navigate to "SSH" and press Enter. This option allows you to enable or disable the SSH service.
- Choose "Yes" to enable SSH and press Enter. This confirms your decision to enable the SSH service.
- If prompted, confirm your selection.
- Exit raspi-config by selecting "Finish" and reboot the Raspberry Pi if prompted. The changes will take effect after a reboot.
Step 2
Verifying the status of the SSH service is crucial to ensure it is active and running.
sudo service ssh status
Executing this command will display the status of the SSH service. If the service is running, you should see a message indicating that SSH is active. If the service is not running, you may need to restart it using sudo service ssh start. If it still doesn't start then verify you've enabled ssh in Step 1 and that there are no other issues.
Setting Up an SSH Client on Windows
Windows 10 and later versions come with a built-in SSH client, simplifying remote access. Additionally, third-party tools like PuTTY provide alternative functionalities.
Using the Built-in SSH Client
The built-in SSH client is a convenient option for quick connections.
- Open the Command Prompt or PowerShell by searching for them in the Windows start menu.
- Type
ssh pi@and press Enter. Replace - When prompted, enter the password. The default password is "raspberry" unless you have changed it, which we strongly recommend. Enter the password carefully, noting that characters will not be displayed as you type.
Using PuTTY
PuTTY is a highly popular SSH client among Windows users, offering more configuration options.
- Download PuTTY from the official website (www.putty.org).
- Launch PuTTY after downloading and installing the application.
- Enter your Raspberry Pi's IP address in the "Host Name (or IP address)" field. This is the primary step for connecting to your device.
- Choose "SSH" as the connection type under "Connection type" in the left-hand panel. This specifies the protocol you want to use for the connection.
- Click "Open" to initiate the connection. This will attempt to establish the SSH session with your Raspberry Pi.
- When prompted, enter your username and password to authenticate with the Raspberry Pi.
Connecting to Raspberry Pi via SSH
Once the setup is complete, connecting to your Raspberry Pi via SSH is a straightforward process. Here's a detailed guide:
Step 1
The IP address is essential for establishing a connection. You can find your Raspberry Pi's IP address in several ways:
You can find your Raspberry Pi's IP address using the terminal on the Raspberry Pi itself:
hostname -I
This command will display the IP address that has been assigned to your Raspberry Pi. Note that the IP address can change if you're using DHCP. We recommend assigning a static IP address.
Step 2
With the IP address, you can connect using your chosen SSH client.
From your Windows machine, open your chosen SSH client (Command Prompt, PowerShell, or PuTTY) and type:
ssh pi@
Replace
When prompted, enter the password, and you will be successfully connected to your Raspberry Pi. If everything is set up correctly, you should see the command prompt of your Raspberry Pi within your SSH client.
Tips for Successful Connections
- Ensure both devices are connected to the same network. This is the foundation for all network-based communication.
- Check your firewall settings to allow SSH traffic through. Ensure that your Windows firewall or any other security software isn't blocking SSH connections. SSH typically uses port 22.
- Consider using a static IP address for your Raspberry Pi to ensure consistent and reliable connections. A static IP prevents the IP address from changing, which can disrupt connections.
Enhancing SSH Security for IoT Devices
In the domain of remote IoT device management, security is paramount. Implement these key measures to elevate your SSH security:
1. Change the Default Password
The default password "raspberry" is a significant security vulnerability. Change this immediately to a strong, unique password. This action prevents unauthorized access.
sudo passwd
Follow the prompts to set a new, secure password. The command will guide you through the process of entering and confirming your new password. Choose a password that is difficult to guess and does not use any personal information.
2. Disable Root Login
To prevent unauthorized access via the root user, disable root login.
sudo nano /etc/ssh/sshd_config
Locate the line "PermitRootLogin" and change it to "no." This prevents direct root login via SSH.
After making this change, restart the SSH service:
sudo service ssh restart
This ensures that the change takes effect immediately. From now on, users will not be able to log in directly as root. Instead, they will need to use their regular user account and then use the `sudo` command to elevate their privileges.
3. Use Public Key Authentication
Public key authentication offers an extra layer of security and eliminates the need for passwords during SSH sessions. This approach strengthens the security posture significantly.
First, generate a key pair on your Windows machine. This involves creating a public and a private key.
ssh-keygen
Follow the prompts. Typically, you can accept the default settings (the location to save the key and an empty passphrase). This command will generate both a public and a private key.
Then, copy the public key to your Raspberry Pi. This involves transferring the public key from your Windows machine to the Raspberry Pi.
ssh-copy-id pi@
Enter your password when prompted.
From then on, you will be able to log in to your Raspberry Pi without needing to enter your password again.
Troubleshooting Common Issues
Despite a thorough setup, problems can still arise. Here are some common issues and their solutions:
Problem
- Verify the IP address of your Raspberry Pi. Double-check that you're using the correct IP address for the Raspberry Pi.
- Ensure SSH is enabled on the Raspberry Pi. As detailed earlier, SSH needs to be activated.
- Check both network connectivity and your firewall settings. Confirm that both your Raspberry Pi and your Windows machine are connected to the same network, and that your firewall allows SSH traffic.
Problem
- Ensure you're using the correct username ("pi" by default, unless you've changed it). Verify your username and make sure you have not changed it.
- Double-check your password or your public key configuration. If using a password, ensure it is correct. If using public key authentication, double-check that the key is correctly configured.
If these suggestions do not resolve your issues, consult the official Raspberry Pi documentation or relevant community forums for further assistance. Online resources can provide more advanced troubleshooting steps.
Alternative Tools for Remote Access
While SSH is the premier choice for remote access, other tools offer viable alternatives, each with their own strengths and weaknesses.
1. VNC Viewer
VNC Viewer provides a graphical interface for remote access. This makes it easier for beginners to grasp, as it provides a visual representation of the remote desktop. This is particularly helpful if you prefer to interact with a graphical user interface (GUI).
2. TeamViewer
TeamViewer offers advanced features, including file transfer and screen sharing. This makes it a solid choice for enterprise-level applications, as well as any scenario where you need to easily transfer files or remotely collaborate. TeamViewer provides additional capabilities beyond simple command-line access.
3. Web-based Solutions
Tools like ngrok or cloud-based services provide remote access without the need for port forwarding or complex configurations. This simplifies the process by handling the technical complexities behind the scenes. These web-based solutions offer ease of setup.
The most appropriate tool for your needs will depend on your specific preferences and requirements. The best solution depends on the individual use case and the expertise of the user.
- Remote Iot Batch Jobs Automate Amp Optimize Your Data Processing
- Jim Cramer Hospitalized Latest Updates Impact On The Financial World