Do you want to harness the full potential of your RemoteIoT devices while guaranteeing top-tier security? In today's interconnected world, mastering Secure Shell (SSH) connectivity isn't merely advantageous; it's an indispensable skill.
Remote access to Internet of Things (IoT) devices has swiftly become the cornerstone of effective system management and monitoring. This guide serves as your comprehensive roadmap to understanding and implementing secure connections. Whether you are a seasoned IT professional or an enthusiastic beginner, the ability to securely access your IoT devices is critical. The widespread adoption of IoT devices across diverse sectors underscores the critical importance of securing remote access. This is particularly important when utilizing technologies such as SSH, a fundamental skill for anyone involved in maintaining secure, efficient, and responsive digital infrastructures.
| Subject: | RemoteIoT Device SSH |
| Description: | A guide to securing RemoteIoT devices using SSH, covering setup, troubleshooting, and best practices. |
| Key Concepts: | SSH, Remote Access, IoT Security, Device Management, Network Protocol |
| Target Audience: | IT Professionals, System Administrators, IoT Enthusiasts |
| Reference: | Wikipedia - Secure Shell |
RemoteIoT devices are fundamentally changing how businesses and individuals interact with technology. These cutting-edge devices empower users to remotely monitor and control systems, offering unparalleled flexibility and control. This capability is increasingly crucial for modern infrastructure management, enhancing operational efficiency, and streamlining critical processes across various industries. It is revolutionizing the approach to data collection, analysis, and action.
- Sone 385 English Sub Global Music Sensation Unveiled
- Hdhub4u 2025 Your Ultimate Streaming Guide Review
These devices are packed with a suite of essential features. Real-time data monitoring offers immediate insight into system performance, enabling proactive adjustments and rapid response to anomalies. Automated system updates ensure devices stay current with the latest software and security patches, thus mitigating vulnerabilities. Remote diagnostics and troubleshooting capabilities facilitate swift identification and resolution of issues, minimizing downtime. Integration with cloud platforms fosters seamless data exchange, enabling advanced analytics and integration with existing business processes. This convergence of functionality enables a new level of operational awareness and control, previously unattainable.
The need to securely connect to these devices is of paramount importance, and SSH (Secure Shell) plays a pivotal role in ensuring data integrity and robust security. This guide will empower you with the necessary skills to manage your RemoteIoT devices effectively, mitigating risks and optimizing network performance. Successfully implementing secure remote access is not merely a technical requirement; it is a fundamental strategic imperative.
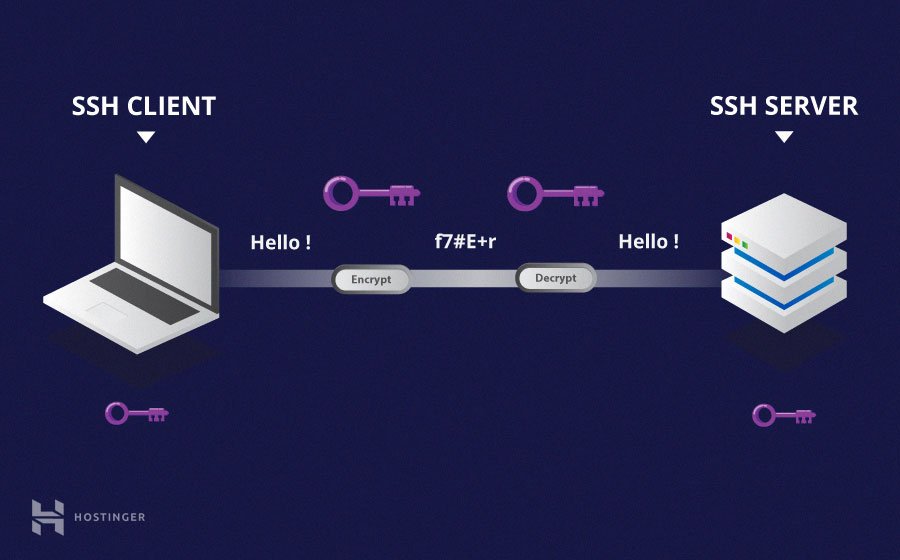
SSH, or Secure Shell, stands as a cryptographic network protocol carefully designed for the secure transmission of data, remote command execution, and the provision of other secure network services. It creates a secure channel over an unsecure network by using encryption on all transmitted data, guaranteeing the privacy and authenticity of your communications. This encryption ensures that any data passing between the user and the IoT device remains confidential and protected from unauthorized access.
- Trwhocom Your Goto For Whois Data Domain Insights
- Movie Rulzla Kannada Is It Safe To Watch Kannada Movies
The benefits of employing SSH in the context of managing RemoteIoT devices are numerous. Data encryption protects sensitive information from prying eyes, ensuring confidentiality. Robust authentication mechanisms verify the identity of users, preventing unauthorized access. Protection against eavesdropping safeguards against data interception. SSH supports secure file transfer, enabling the safe exchange of files between your device and remote systems. By using SSH, you can rest assured that your connection is fortified against unauthorized access, effectively thwarting potential data breaches and maintaining the integrity of your IoT infrastructure. This provides peace of mind and reliability in critical operations.
Before diving into the practical aspects of connecting to your RemoteIoT device via SSH, it's essential to ensure you have the necessary prerequisites. This will streamline the setup process, ensuring a smooth and efficient experience. Proper preparation lays the groundwork for a successful and secure connection.
To begin, you will need the appropriate hardware, beginning with a computer or laptop equipped with an SSH client. This client serves as the interface for establishing the secure connection. A stable internet connection is essential, as it forms the pathway for remote access. Lastly, your RemoteIoT device must be configured with SSH enabled. This setting is fundamental for accepting and processing SSH connection requests. Ensuring these elements are in place will allow for a seamless setup.
On the software side, you'll need an SSH client. Popular choices include PuTTY for Windows users and the built-in OpenSSH client available on Linux and Mac systems. In addition to a functional SSH client, you will need access credentials for the RemoteIoT device. These credentials typically include a username and password, which are used to authenticate your identity and grant access to the device's command-line interface. Having the right software and credentials is key to establishing a secure and efficient connection.
This tutorial provides a structured, step-by-step guide to help you establish a secure SSH connection to your RemoteIoT device. Each step is designed to be easy to follow, enabling even those new to SSH to configure and manage their devices securely. Following these steps in sequence will guide you through the process in a clear and efficient manner.
First, install an SSH client appropriate for your operating system. For those on Windows, PuTTY offers a reliable graphical interface. Linux and Mac users typically have OpenSSH pre-installed, simplifying the initial setup process. You'll find that installing an SSH client is a crucial first step in establishing a secure connection. Choosing the right client for your system ensures compatibility and ease of use.
Then, gather the necessary device information. This includes the IP address of your RemoteIoT device and its login credentials. You'll generally find this information in the device's documentation or from your network administrator. The IP address is the device's unique identifier on the network, and the login credentials verify your identity. Having this information readily available will streamline the connection process.
Next, establish the connection. Open your SSH client of choice and enter the IP address of the RemoteIoT device in the designated field. When prompted, enter the device's username and password to authenticate. Upon successful authentication, the client establishes a secure SSH connection. Following these steps accurately will help establish the crucial connection.
Finally, verify the connection. Once connected, you should be able to access the device's command-line interface (CLI). Test that you can execute basic commands. Successful interaction at this stage confirms a stable and functional SSH connection, validating that everything is working correctly. This confirmation is essential to ensure all components are working as expected.
During the process of setting up an SSH connection to your RemoteIoT device, it is possible to encounter common issues. These challenges are often easily resolved with a systematic approach to troubleshooting. Here are some common issues and troubleshooting tips to guide you. Recognizing these issues early can help you mitigate potential problems.
If you encounter a "Connection Refused" error, it indicates that the SSH service on your RemoteIoT device may not be running or accessible. First, verify that the SSH service is active on the device. Second, check your firewall settings to ensure that they allow incoming connections on port 22, which is the standard port used by SSH. Addressing these points often resolves the "Connection Refused" error efficiently.
An "Authentication Failure" error suggests a problem with your login credentials. Double-check the username and password for accuracy, paying close attention to capitalization and special characters. If you're using key-based authentication, confirm that your SSH keys are correctly configured on both your client and the RemoteIoT device. Correctly verifying your credentials is the first step to resolving this issue.
Network connectivity issues can also disrupt your connection. Ensure that your internet connection is stable and functional. Confirm that the IP address of your RemoteIoT device is correctly entered in your SSH client. Also, consider pinging the device's IP address to confirm its presence on the network. Assessing network stability can prevent future interruptions.
Implementing robust security measures is critical when dealing with remote access to your IoT devices. Here's a compilation of the best practices to ensure the security of your SSH connections, minimizing risks and enhancing the integrity of your IoT ecosystem. These practices are crucial for securing any remote access setup.
Use strong, unique passwords that are difficult to guess or crack. Avoid using easily guessable words or default credentials that are readily available. A robust password is your first line of defense against unauthorized access. Protecting your credentials from unwanted access is paramount.
Enable key-based authentication. This method replaces password authentication with cryptographic keys, providing an added layer of security and reducing the risk of brute-force attacks. Using keys provides a secure and strong alternative to passwords.
Limit SSH access to trusted IP addresses. Restricting access to a specific list of known IP addresses prevents unauthorized connections from outside sources. Consider disabling root login to further minimize potential risks. Restricting access enhances the security posture of any system.
After mastering the basics, you can move forward with advanced configurations. These configurations will optimize your RemoteIoT device's performance and strengthen its security posture. Advanced configurations are essential for gaining deeper control over your systems.
Set up port forwarding on your router. This allows secure external access to your RemoteIoT device. Forwarding the correct port ensures that external connections are directed to the correct device on your network. Setting up port forwarding is essential to remotely manage devices.
Use SSH tunneling to securely access services running on the RemoteIoT device. SSH tunneling encrypts the traffic, providing an extra layer of security, and can be used to access internal resources such as databases or web servers. Tunneling allows secure access to internal resources.
Configure automated backups to ensure your device's data is regularly saved and accessible in case of failure. Automated backups protect against data loss and help restore your system quickly. Backups are crucial for disaster recovery.
Several tools and software can significantly enhance your experience when working with RemoteIoT devices over SSH. These tools streamline processes, facilitate advanced configurations, and provide critical insights into your system's performance. Utilizing the right tools can make the difference in efficiency.
SSH Clients are essential for establishing a connection to your RemoteIoT device. PuTTY remains a popular choice for Windows users. For Linux and Mac users, the built-in OpenSSH client provides seamless integration and extensive functionality. Choosing the right client streamlines the process.
Monitoring Tools provide valuable insights into your device's performance and help identify potential issues before they escalate. Netdata and Prometheus are powerful tools for gathering and visualizing system metrics, offering a comprehensive view of your device's operation. Monitoring tools help detect potential problems and improve reliability.
SSH is versatile and can be applied to a wide range of use cases involving RemoteIoT devices. These applications span various industries and domains, illustrating the technology's adaptability and the value it brings. Understanding the different application of SSH offers a new perspective on how the technology can be deployed.
In industrial automation, SSH allows you to remotely monitor and control industrial equipment, optimizing performance and reducing downtime. It facilitates remote diagnostics, helping you to identify and address issues promptly, improving efficiency and minimizing operational disruptions. SSH enables you to maintain constant supervision of essential equipment.
In smart home systems, you can access and manage smart home devices such as thermostats and security systems from anywhere in the world. This level of remote access offers unprecedented convenience and control, simplifying daily tasks and providing peace of mind. Remotely managing smart home devices provide you peace of mind while simplifying daily tasks.
In environmental monitoring, SSH enables you to collect and analyze data from sensors deployed in remote locations. This provides critical insights for environmental research, allowing you to gather data from difficult-to-reach locations and providing the basis for informed decisions. SSH facilitates research and data collection.
As technology evolves, the role of SSH in securing IoT devices will become even more crucial. Upcoming trends aim to enhance security, efficiency, and performance. The integration of SSH into IoT devices is not just a trend; it's becoming essential for securely managing, controlling, and protecting these connected systems. The future of SSH looks bright, with innovation driving the technology forward.
Quantum-resistant encryption focuses on developing encryption methods capable of withstanding quantum computing attacks, ensuring long-term security for IoT devices. The anticipated arrival of quantum computers calls for more advanced security strategies. Anticipating future technology and security threats are essential.
AI-Driven Security utilizes artificial intelligence to detect and respond to security threats in real-time, boosting the protection of IoT networks. AI's ability to identify patterns and anomalies can help improve the responsiveness of IoT devices. Leveraging AI offers new solutions to mitigate security threats.
5G Connectivity leverages the increased bandwidth and reduced latency of 5G networks to improve the performance and reliability of remote IoT connections. 5G offers faster and more reliable remote control options than ever before. 5G is essential for performance and reliability of remote IoT connections.
- 9xmoviescom Is It Legal Safe Streaming Risks Alternatives
- Discover Kannada Movierulz History The Future Of Sandalwood