Can you truly afford to ignore the security of your interconnected devices in today's digital age? The answer, quite simply, is no. Protecting your Internet of Things (IoT) devices isn't just a good idea; it's an absolute necessity, and the proliferation of smart devices demands that we prioritize the security of communication between them.
Securing an IoT environment might seem complex, particularly for those new to the intricacies of this technological landscape. However, the principles are understandable and the implementation, while requiring diligence, is achievable. This article aims to provide a comprehensive guide to securing remote IoT devices within a Virtual Private Cloud (VPC), utilizing the Raspberry Pi platform. We'll delve into essential concepts, practical techniques, and freely available resources, all geared towards safeguarding your data and infrastructure. This guide will offer actionable insights, empowering you to protect both your devices and the sensitive information they handle.
To provide a structured overview, let's begin with a summary of the topics we will be covering in detail:
- 9xmovies 2025 Is It Safe Legal For Movie Streaming
- Is Dwayne Johnson Dead Debunking The Rumors Celebrating The Rock
| Topic | Description |
|---|---|
| IoT Security Fundamentals | Understanding the core principles of securing IoT devices and their networks. |
| Virtual Private Cloud (VPC) Setup | Creating a secure, isolated network for your IoT devices. |
| Raspberry Pi Integration | Using the Raspberry Pi to establish secure IoT connections. |
| Free Download Resources | Exploring freely available tools and resources to enhance your IoT security. |
| Secure Communication Protocols | Implementing secure protocols such as MQTT and HTTPS. |
| Best Practices | Adopting essential security measures for your IoT VPC connections. |
| Future Trends | Discussing emerging technologies and the evolving nature of IoT security challenges. |
Let's embark on this journey into the critical realm of IoT security.
Understanding IoT Security and Its Importance
- 5movierulzcom Kannada 2023 Risks Alternatives You Need To Know
- Discover Kannadamovierulz Your Guide To Kannada Cinema
At its core, IoT security involves the technologies and methodologies used to safeguard Internet of Things devices, including the networks they connect to. From the unassuming smart thermostat controlling your home's temperature to the advanced industrial sensors that monitor critical infrastructure, these devices frequently operate with minimal inherent security measures, making them attractive targets for malicious cyberattacks. Therefore, securing remote IoT devices is vital to protect sensitive data and mitigate the risk of unauthorized access.
The significance of IoT security is magnified by the increasing integration of IoT devices within critical systems. Consider their applications in healthcare, where patient monitoring devices collect sensitive health data, or in manufacturing, where industrial sensors control vital processes. A single security breach can lead to a catastrophic chain of events, potentially resulting in data theft, significant financial losses, and even endangerment of human lives. By ensuring the security of remote IoT VPC connections, you can achieve several critical objectives:
- Protect Confidential Information: Shield sensitive data from unauthorized access, safeguarding privacy and ensuring confidentiality.
- Prevent Malicious Takeover: Prevent malicious actors from gaining control of your devices, which will hinder their capacity to cause harm.
- Ensure Regulatory Compliance: Meet industry-specific regulations and standards, and avoid potential legal repercussions.
Identifying and understanding potential threats is the initial step in fortifying your IoT environment. Some of the most prevalent threats include:
- Device Hijacking: Attackers take control of IoT devices, utilizing them for malicious purposes, such as launching attacks or stealing data.
- Data Breaches: Unauthorized access to sensitive data transmitted between devices, exposing confidential information to potential compromise.
- Firmware Vulnerabilities: Exploiting outdated or unpatched firmware to infiltrate devices, gain control, or extract valuable information.
Setting Up a Virtual Private Cloud (VPC) for IoT Devices
A Virtual Private Cloud (VPC) serves as a secure and isolated network environment, offered by major cloud service providers. Imagine it as a private network within a larger public cloud environment. This setup enables you to host and manage your IoT devices within a controlled, private space. This ensures secure communication between devices, shielded from external threats and unauthorized access. Effectively, using a VPC creates a virtual perimeter surrounding your IoT devices.
The advantages of using a VPC for IoT deployments are significant and compelling:
- Enhanced Security: Network isolation forms the basis of enhanced security, reducing the potential attack surface and thwarting unauthorized access.
- Flexible Configuration: VPCs provide a wide range of configuration options, enabling precise device management and highly customized network configurations.
- Scalability: VPCs offer the scalability needed to accommodate the expansion of your IoT deployments, allowing for effortless adaptation as your requirements change and grow.
Creating a VPC for your IoT devices generally entails the following steps:
- Cloud Provider Selection: Choose a cloud provider that supports VPC creation, such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP). Each provider offers different pricing models and features. Therefore, select the one that aligns best with your specific requirements.
- Network Parameter Definition: Define your network parameters, including IP address ranges (CIDR blocks) and subnets. This determines the logical structure of your network within the VPC. Meticulous planning here is critical for ensuring future expansion and security.
- Security Group and Access Control List (ACL) Configuration: Configure security groups and access control lists (ACLs) to control network traffic and restrict unauthorized access. Security groups act as virtual firewalls for your instances, while ACLs offer an additional layer of network traffic filtering.
- IoT Device Deployment and Connectivity Testing: Deploy your IoT devices within the VPC and perform thorough connectivity testing. Ensure that your devices can communicate with each other and with necessary resources within the VPC, such as databases or servers. Regularly monitor this connectivity to maintain optimal performance.
Using Raspberry Pi for Secure IoT Connections
The Raspberry Pi, known for its compact size, low cost, and impressive versatility, has become a cornerstone of the maker community. Its adaptability makes it an ideal platform for IoT projects, offering a powerful combination of hardware and software flexibility. The Raspberry Pi's compatibility with a wide range of operating systems and programming languages makes it an excellent choice for establishing secure connections between IoT devices and a VPC. This feature enables custom configurations and provides a high degree of control over the devices' behavior.
Setting up your Raspberry Pi for secure IoT connections is a relatively straightforward process:
- Operating System Installation: Install an operating system on your Raspberry Pi, such as Raspbian (the official Raspberry Pi OS) or Ubuntu. The best choice depends on your specific preferences and the requirements of your project.
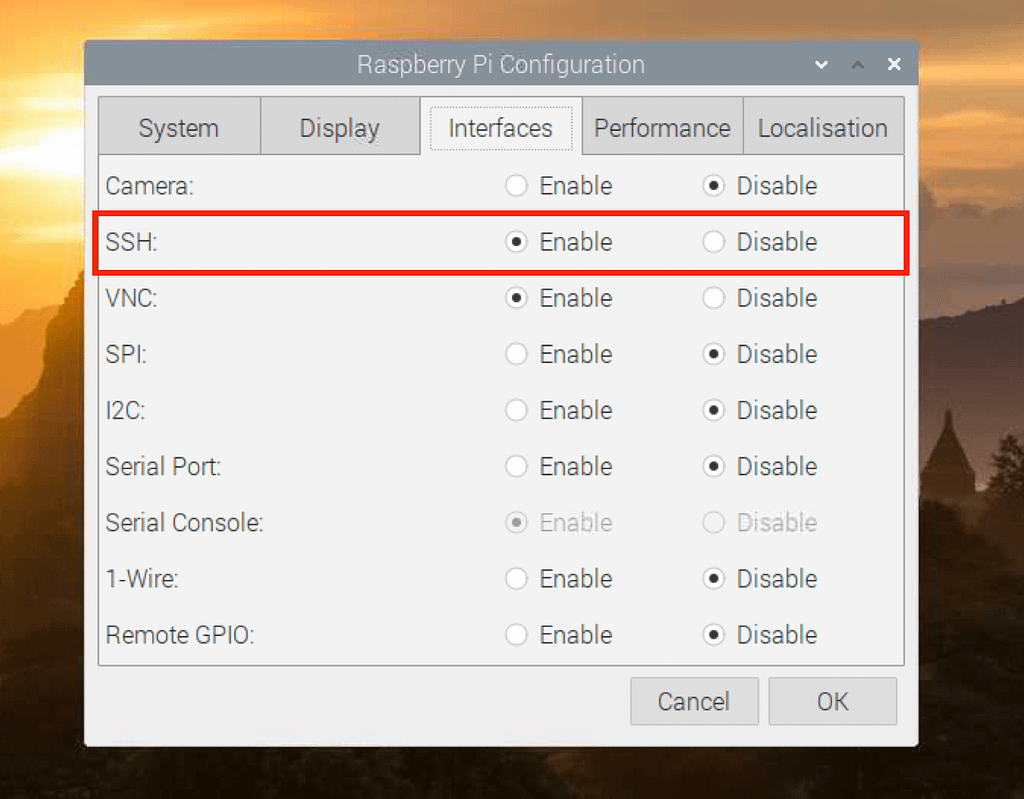
- SSH Configuration and Security Hardening: Configure SSH (Secure Shell) for remote access. This enables remote management of your Raspberry Pi. It is essential to secure SSH with robust authentication methods, such as key-based authentication rather than password-based login.
- Software Package Installation: Install necessary software packages, such as MQTT brokers (Mosquitto, HiveMQ) or SSL/TLS libraries (OpenSSL, GnuTLS), to facilitate secure communication. This software will handle encryption and the secure exchange of data.
- Connection Testing: Conduct thorough testing of the connection between your Raspberry Pi and your IoT devices. Verify that data is being transmitted and received correctly and that communication is secure. Regular testing and monitoring are essential for identifying and addressing any potential issues.
Securing your Raspberry Pi for IoT deployments involves adhering to a set of best practices that should be meticulously followed:
- Strong Credentials: Change the default passwords and use strong, unique credentials for all accounts, including SSH and any applications you install. This is your first line of defense against unauthorized access.
- Regular Updates: Regularly update the operating system and all installed software to patch newly discovered vulnerabilities. This includes both security patches and firmware updates. Automate updates where possible to streamline the process.
- Firewall and Intrusion Detection Systems: Implement firewalls and intrusion detection systems to monitor and block suspicious activities. Configure your firewall to restrict network traffic to only the necessary ports and protocols. Consider utilizing tools like fail2ban to automatically block IP addresses that attempt to brute-force passwords.
Free Download Resources for Secure IoT Connections
Fortunately, securing your IoT setup doesn't necessarily demand the use of expensive proprietary software. A vast array of free and open-source tools are available, allowing you to establish secure connections between your remote IoT devices and a VPC utilizing a Raspberry Pi. These tools offer a cost-effective method for implementing robust security measures.
Here are some popular free options:
- MQTT Brokers: Mosquitto and HiveMQ offer free versions suitable for small-scale deployments. MQTT is a lightweight messaging protocol that is ideally suited for resource-constrained IoT devices.
- Encryption Libraries: OpenSSL and GnuTLS provide powerful encryption capabilities, enabling you to secure data transmission.
- Network Monitoring Tools: Wireshark and Nmap are invaluable for identifying and mitigating potential security threats. These tools enable you to analyze network traffic, identify vulnerabilities, and actively monitor your network for malicious activity.
Choosing the right tools for your IoT project requires careful consideration of several factors:
- Compatibility: Ensure compatibility with your Raspberry Pi and the IoT devices you intend to connect. Confirm that the tools support the operating system and hardware you are using.
- Ease of Use: Opt for tools that are relatively easy to install and configure, particularly if you're new to the field. Look for good documentation and community support to assist you.
- Community Support: Consider the level of community support and the availability of comprehensive documentation. A strong community can provide valuable assistance when you encounter challenges.
To maximize the effectiveness of free tools in securing your IoT environment, it's essential to follow these best practices:
- Keep Updated: Regularly update all tools to ensure you have the latest security patches. Software vendors routinely release updates to address vulnerabilities.
- Documentation: Document your configurations and settings thoroughly for future reference. This will aid in managing and troubleshooting your system efficiently.
- Testing: Test all tools within a controlled environment before deploying them in a production setting. This practice enables you to identify potential issues without risking the security of your live IoT setup.
Implementing Secure Communication Protocols
Secure communication protocols are the vital elements in protecting the data transmitted between IoT devices and a VPC. These protocols ensure that the exchanged information remains confidential and unaltered throughout its entire journey. The selection of a specific protocol should align with the unique requirements of your IoT devices, taking into consideration factors such as power consumption, bandwidth limitations, and security needs. Selecting the correct protocol is critical for establishing a robust and secure IoT deployment.
Here are some commonly used protocols to consider:
- MQTT (Message Queuing Telemetry Transport): A lightweight protocol perfectly suited for resource-constrained devices that have limited processing power and network bandwidth. MQTT is a popular choice for various IoT applications.
- CoAP (Constrained Application Protocol): Specifically designed for low-power and low-bandwidth networks, making it an ideal choice for devices in challenging environments. CoAP is commonly utilized in sensor networks.
- HTTPS (HTTP Secure): Provides secure web communication via SSL/TLS encryption. HTTPS offers a strong and well-established method for encrypting data transmitted over the internet.
Configuring MQTT for secure communication demands meticulous attention to detail:
- MQTT Broker Installation: Install an MQTT broker on your Raspberry Pi or a cloud-based server. The broker acts as a central point for message exchange between devices.
- SSL/TLS Encryption: Enable SSL/TLS encryption to secure data transmission. This safeguards your data from eavesdropping and potential tampering.
- Authentication: Set up username and password authentication to control access to the MQTT broker, ensuring only authorized devices can connect. This prevents unauthorized devices from accessing your network.
Data integrity is another crucial aspect of IoT security. Ensuring that data remains unaltered during transmission is of paramount importance. To protect data integrity, adopt the following strategies:
- Digital Signatures: Utilize digital signatures to verify the authenticity of data. This guarantees that the data originates from a trusted source and has not been tampered with during transit.
- Checksums: Implement checksums to detect and correct errors that may occur during data transmission.
- Regular Audits: Regularly audit logs to identify and address any discrepancies or inconsistencies. Review logs for any unusual activity or potential errors.
Best Practices for Securing IoT VPC Connections
Implementing robust security measures is absolutely essential for safeguarding your IoT devices and the data they generate. Here are several key best practices that, when implemented collectively, will significantly enhance the security posture of your IoT VPC connections:
Network Segmentation: Network segmentation is a fundamental security practice. This involves dividing your network into distinct zones, employing techniques such as VLANs or subnets. This isolation ensures that IoT devices are separated from other critical systems, notably reducing the risk of lateral movement, in which a compromised device could be used to attack other areas of the network. It is a key element of a defense-in-depth approach.
Regular Security Audits: Routine security audits are a crucial step for identifying vulnerabilities and maintaining compliance with security standards. Schedule regular audits to evaluate the security posture of your IoT environment. Consider automating these audits by employing tools like Nessus or OpenVAS to streamline the process. This practice allows for a faster identification and remediation of any identified vulnerabilities. Regular audits keep you proactive, rather than reactive, in your approach.
Employee Training and Awareness: The human factor frequently represents the weakest link in any security chain. It is essential to educate your team about IoT security best practices, and consistently encourage them to promptly report any suspicious activities. Conduct regular training sessions, concentrating on critical topics like password security, phishing awareness, and the importance of consistently updating software. A well-informed team serves as a robust defense against security threats.
Continuous Monitoring: Implement continuous monitoring of your IoT environment. Utilize intrusion detection systems (IDS) and intrusion prevention systems (IPS) to detect and proactively prevent malicious activities. Regularly review logs to identify unusual events, unauthorized access attempts, and any other potential signs of compromise. Constant vigilance is essential for maintaining a secure IoT infrastructure.
Strong Authentication and Authorization: Enforce robust authentication mechanisms, such as multi-factor authentication (MFA), to verify user identities. Implement robust authorization controls to limit access to sensitive data and system resources. Adhere to the principle of least privilege, providing users with only the minimum permissions required to perform their assigned tasks.
Secure Configuration Management: Employ secure configuration management practices to proactively safeguard your IoT systems. Implement configuration management tools to automate the process of securing and meticulously maintaining your IoT devices. Ensure that all configurations are securely stored and are subject to version control. Regularly review and update configurations to swiftly address any security vulnerabilities that may emerge.
Data Encryption: Encrypt sensitive data both during transit and while at rest. Employ strong encryption algorithms to protect data from unauthorized access. Encrypt data transmitted between IoT devices and the VPC, and also encrypt any data stored on the devices themselves and within the cloud environment. Encryption is an essential and integral element of comprehensive data protection.
Future Trends in IoT Security
The landscape of IoT security is a dynamic, rapidly evolving domain. To stay ahead of emerging threats, it is imperative to remain informed about the latest trends and technological advancements that are reshaping the future of this critical field.
Emerging technologies are poised to revolutionize the future of IoT security:
- Blockchain: Blockchain technology is showing significant promise in providing decentralized, tamper-proof data storage. Blockchain's inherent properties of immutability and transparency can greatly improve data integrity and overall security within IoT environments.
- AI and Machine Learning: AI and machine learning are being actively used to enhance threat detection and improve response capabilities. These technologies can analyze vast amounts of data to identify anomalies and proactively predict potential security threats.
- Quantum Cryptography: Quantum cryptography offers unparalleled encryption strength, providing unprecedented security for communications. As quantum computing technology advances, the need for quantum-resistant cryptography will become increasingly important.
The regulatory landscape for IoT is in a constant state of evolution. As the adoption of IoT devices accelerates, governments and organizations are developing regulations to ensure data privacy and security. These regulations, like the GDPR (General Data Protection Regulation) and the CCPA (California Consumer Privacy Act), impose specific requirements on how organizations collect, store, and process personal data. Remaining informed about these regulations is crucial for maintaining compliance and avoiding potential legal and financial repercussions.
The evolving threat landscape presents continuous and persistent challenges. Staying current with the latest security trends and investing in essential tools and comprehensive training is essential to effectively address these emerging challenges. This includes actively monitoring the security industry, attending relevant conferences and training programs, and continuously updating your knowledge and skillset.
- Hdhub4u South Hindi Your Guide To Streaming South Hindi Movies
- Discover Kannada Movierulz History The Future Of Sandalwood