In an era where the digital landscape expands exponentially, are our remote Internet of Things (IoT) devices truly secure, or are they vulnerable entry points for malicious actors? The answer, a resounding affirmative, lies in proactive security measures. The convergence of a Virtual Private Cloud (VPC) and a Raspberry Pi has emerged not just as a technical solution, but as a fundamental skill for developers and technology enthusiasts navigating the complexities of a hyper-connected world. Securing these devices isn't a luxury; it is the very bedrock upon which a secure and reliable IoT ecosystem is built. This in-depth exploration will illuminate the pathway, providing a meticulous framework for establishing secure connections for your IoT devices using the versatile Raspberry Pi, while simultaneously revealing a wealth of freely available resources to empower your projects.
This guide is crafted to empower you, regardless of your experience. We will dissect step-by-step instructions and provide insightful guidance, demystifying the intricacies of securing IoT devices. By the end of this article, you will possess a comprehensive understanding of how to construct a secure and resilient environment for your IoT ventures. This is not mere theoretical discussion; it is firmly grounded in practical solutions, real-world examples, and the wisdom of industry experts. We will meticulously analyze both the 'how' and the 'why', ensuring your IoT setup is both secure and efficient. The focus is on providing actionable, immediately applicable intelligence. Let us embark on this journey, exploring how to achieve a secure connection for your remote IoT devices using a Raspberry Pi, transforming potential weaknesses into unassailable strengths.
This material is provided for informational purposes only. Neither the author(s) nor the publisher(s) of this content offer any warranties regarding its content, including its accuracy or usefulness. This information is intended to inform readers, not to provide specialized advice on technology or internet privacy. Readers are strongly advised to consult with qualified professionals for specific guidance.
- 5movierulz Kannada Movies In 2023 Watch Legally Stay Informed
- Alex Wagners Illness What You Need To Know Updates
A Virtual Private Cloud (VPC) is the cornerstone of securing IoT devices, providing a protected environment where your IoT devices can communicate securely, shielded from unauthorized access. By strategically implementing a VPC, you gain the ability to meticulously control access to your devices, ensuring that only those with proper permissions can interact with them. This level of control is critical in any setting where the integrity of your data and the security of your operations are of utmost importance. The VPC provides a layer of defense that is absolutely indispensable in the modern IoT landscape.
Why Leverage a VPC for IoT Projects?
Adopting a VPC for your IoT projects offers a multitude of significant advantages:
- Enhanced Security: Isolates your devices from the public internet, significantly reducing the attack surface and lessening the likelihood of security breaches.
- Improved Performance: VPCs frequently contribute to lower latency and more efficient data transfer, leading to improved responsiveness and enhanced overall performance.
- Granular Control: VPCs empower you with precise control over network traffic and access permissions, allowing you to tailor your security protocols to the specific requirements of your IoT ecosystem.
VPCs are especially valuable when managing remote IoT devices that exchange data frequently. They create a secure and reliable connection, ensuring your devices function seamlessly, even in the most demanding environments. The combination of security, performance, and control makes the VPC a critical component for any serious IoT deployment.
The Raspberry Pi, a versatile and budget-friendly single-board computer, has become a preferred choice for managing and securing IoT devices. Setting up a Raspberry Pi for IoT projects involves a series of steps, starting with hardware configuration and progressing to software installation. The Raspberry Pi's adaptability and ease of use make it ideal for both beginners and seasoned developers. It's the perfect entry point for secure and efficient IoT development.
Raspberry Pi Setup
Heres a detailed guide to setting up your Raspberry Pi:
- Install the latest version of Raspberry Pi OS: The operating system forms the very foundation of your system. Download the OS image from the official Raspberry Pi website and "flash" it (write it) onto your SD card. Ensure you choose the correct version for your specific Pi model.
- Connect your Raspberry Pi: Connect your Raspberry Pi to a monitor, keyboard, and mouse to allow for direct interaction with the system.
- Update the operating system: Once the OS is installed, update the OS using the following commands in the terminal:
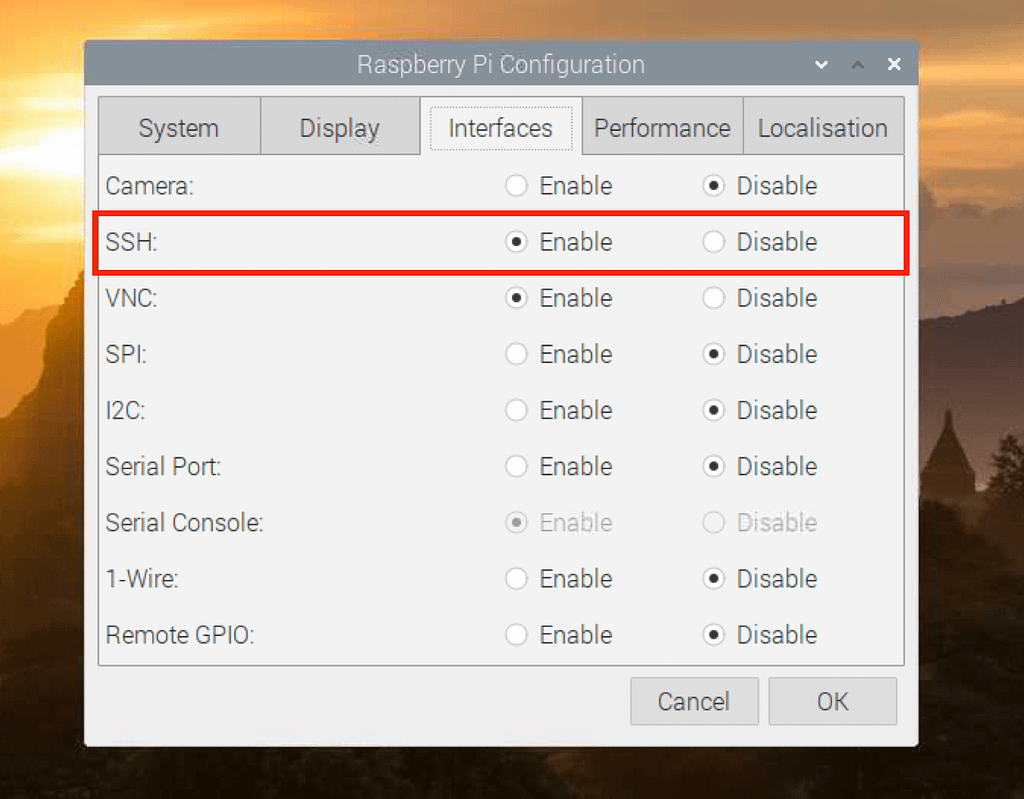
sudo apt update && sudo apt upgrade. This ensures that your system is equipped with all the necessary packages. - Install SSH and VNC: Install software packages such as SSH (Secure Shell) and VNC (Virtual Network Computing) for remote access. SSH allows you to securely access the command line remotely. VNC allows you to see and control the Raspberry Pi's graphical desktop.
Once your Raspberry Pi is configured, you can move onto the more complex task of setting up IoT applications. This ensures your Raspberry Pi is fully prepared to communicate with your VPC, ready to play a critical role in your secure IoT environment.
Securing communication between IoT devices and your VPC is paramount to safeguarding sensitive data. Several protocols can be employed to achieve this, including MQTT, HTTPS, and TLS. The right choice of protocol can significantly impact your system's overall security. A well-chosen protocol will minimize the risks associated with unauthorized access and data breaches.
Choosing the Right Communication Protocol
Each protocol is designed with specific strengths and weaknesses in mind:
- MQTT (Message Queuing Telemetry Transport): A lightweight protocol, perfectly suited for low-bandwidth environments. Its efficiency makes it ideal for devices with limited resources.
- HTTPS (Hypertext Transfer Protocol Secure): A secure web communication protocol. It encrypts data transmitted between the device and the server, protecting the integrity and confidentiality of communications.
- TLS (Transport Layer Security): TLS provides end-to-end encryption. This ensures data is encrypted from the source to the destination, adding an extra layer of security for all data transfer types.
The optimal protocol will depend on the unique needs of your IoT project. Careful consideration should be given to factors like bandwidth restrictions, security requirements, and the nature of the data being transmitted. A comprehensive evaluation is critical before selecting your communication protocol.
Configuring a VPC for IoT involves setting up subnets, security groups, and access control lists, all vital components for secure device communication. These elements ensure that data transfers between devices are secure and protected from potential intrusions. Configuration is an essential, non-negotiable step in the process; without it, a VPC cannot deliver the security it promises.
Key Steps in VPC Configuration
Here are the essential steps to configure your VPC:
- Create a VPC with a unique CIDR block: The CIDR block (Classless Inter-Domain Routing block) must be carefully chosen to provide an adequate address space for your devices. The VPC creation itself is the initial step.
- Set up public and private subnets: Subnets segregate device traffic. Public subnets can host resources accessible from the internet, whereas private subnets isolate resources that should not be directly exposed.
- Configure security groups: Security groups govern which traffic is allowed to and from your devices. They effectively function as virtual firewalls.
- Use NAT gateways: NAT (Network Address Translation) gateways allow private devices to securely access the internet. This is particularly useful when devices in private subnets need to download software updates.
By following these steps, you'll create a robust VPC environment specifically tailored to your IoT requirements. These actions guarantee the protection of your data. Your system will be strong, prepared to meet the challenges of a secure and effective IoT deployment.
Remote access is fundamental for the management of IoT devices deployed in remote locations. Several tools and techniques can be used to achieve secure remote access, including SSH, VPN, and cloud-based services. The ability to remotely manage your devices is crucial for maintenance, troubleshooting, and ongoing monitoring. The right approach to remote access ensures you maintain control of your devices, regardless of their geographical location.
Choosing the Right Tools for Secure Remote Access
Consider these tools for secure remote access:
- SSH (Secure Shell): Provides access to your remote devices from a secure command line. SSH utilizes robust encryption, enabling the safe transfer of data.
- VPN (Virtual Private Network): Offers encrypted access to your VPC from virtually anywhere. A VPN establishes a secure tunnel for all your network traffic.
- Cloud Services: Platforms like AWS IoT Core offer built-in remote access functionality, which streamlines the access management process, with numerous features specifically for IoT devices.
Each tool offers its own benefits, so choose the one that best aligns with your project's needs. The specifics of your project, the nature of your devices, and the overall security landscape, will dictate the choice of the most appropriate tools. Carefully evaluate each option, considering your requirements and constraints, and select the one that offers the best fit.
A wealth of free resources is readily available to enhance your IoT projects. From open-source software to comprehensive online tutorials, these resources can significantly lower development costs while providing invaluable insights and knowledge. Leveraging these free resources is a smart strategy to accelerate your learning curve and minimize the financial outlay required by your project. There are numerous resources to help you get started, and the opportunities for learning are almost limitless. The available resources are more than adequate to meet your needs.
Leveraging Free Resources for IoT Success
Here are some of the best free resources for IoT:
- Raspberry Pi Documentation: Comprehensive guides and tutorials for setting up and using the Raspberry Pi. These resources provide in-depth information on all aspects of the Pi.
- MQTT Eclipse: Provides open-source MQTT broker and client tools. Excellent for those needing robust messaging solutions.
- GitHub Repositories: A vast collection of IoT projects and code samples. GitHub offers readily available examples and templates to jumpstart your development process.
By leveraging these resources, you can accelerate your IoT development and improve your outcomes. With consistent and disciplined use of these valuable resources, you'll find your projects progressing at a faster rate.
Even with meticulous planning, problems can arise when setting up and managing IoT devices. Understanding these potential issues, alongside their solutions, will improve your troubleshooting effectiveness. Being prepared to address these problems is essential for maintaining a stable and secure IoT environment. These problems may occasionally surface, but with preparation, you can tackle them effectively.
Troubleshooting
Here are some common issues and their solutions:
- Connection Failures: Always verify network settings and ensure all devices are configured correctly. Take the time to methodically confirm your network configuration.
- Security Breaches: Regularly update your software and always utilize robust encryption protocols. Security vulnerabilities can be addressed through regular updates, and its important to remain vigilant.
- Performance Issues: Optimize data transfer and minimize unnecessary network traffic. Improving system efficiency involves optimizing the data transfer process and reducing any excess traffic.
By promptly addressing these issues, you can maintain a stable and secure IoT environment. The key is to be aware of potential problems and have a proactive plan in place. Swift action is often the key to a successful resolution.
Implementing best practices within your IoT devices is essential for ensuring their security. These practices span everything from device configuration to comprehensive network management. Prioritizing security is not an option; it's a fundamental requirement for any IoT deployment. These steps are crucial for those who want to build and run a safe, reliable IoT system. By following these best practices, your efforts will be well-placed.
Best Practices
Here are some best practices to follow:
- Regularly update firmware and software: Doing so is the only reliable way to defend against vulnerabilities.
- Utilize strong passwords and multi-factor authentication: Limit unauthorized access and enforce strong security protocols.
- Monitor network traffic: Constantly scrutinize for any suspicious activity and respond quickly to potential threats. Understanding whats happening within your network is critical.
Adhering to these practices will enable you to maintain a secure and dependable IoT infrastructure. By adopting these strategies, you'll establish a resilient and secure system.
Examining real-world examples provides valuable insights into effectively implementing secure IoT solutions. These case studies highlight the challenges and solutions encountered in diverse industries. Studying these examples offers inspiration and guidance. Knowing how others have solved their own problems is incredibly valuable.
Real-World Applications
The agricultural industry now employs IoT devices to monitor vital parameters such as soil moisture, temperature, and other critical environmental factors. Securely connecting these devices to a VPC with a Raspberry Pi allows farmers to make data-driven decisions that optimize crop yields, increase efficiency, and improve resource management. In agriculture, this technology is transforming how crops are grown. A well-designed and secure system supports farmers in increasing their productivity, enhancing sustainability, and ensuring the availability of resources.
| Category | Details | Relevance to IoT Security | Example |
|---|---|---|---|
| VPC Configuration | Setting up subnets, security groups, and access control lists within a virtual private cloud. | Provides isolation and security by controlling network traffic and device access, ensuring secure communication and the ability to segregate IoT devices from the broader internet. | Creating a private subnet dedicated to IoT devices and applying strict access restrictions via security groups that allow only authorized traffic. |
| Secure Communication Protocols | Implementing encryption protocols like MQTT, HTTPS, and TLS (Transport Layer Security). | Protects data during transit, ensuring the confidentiality and integrity of the data exchanged between devices, the Raspberry Pi, and the cloud. | Using TLS to encrypt data transmitted from a sensor to the cloud platform, protecting it from eavesdropping and tampering. |
| Raspberry Pi Setup | Installation of the operating system, updating software packages, and enabling secure remote access. | The Raspberry Pi serves as a secure gateway and management point, controlling access and facilitating secure device management. | Configuring SSH access to the Raspberry Pi for secure remote control and management using strong authentication methods. |
| Authentication and Authorization | Implementing strong passwords, multi-factor authentication, and strict access control measures. | Preventing unauthorized access to devices and sensitive data by verifying user identity and enforcing role-based access controls. | Requiring multi-factor authentication (e.g., password and a one-time code) for all users accessing the IoT management console. |
| Regular Updates and Patching | Keeping all firmware and software components up-to-date with the latest security patches. | Mitigating known vulnerabilities in both the devices and the supporting infrastructure and ensuring the continued security and stability of all devices. | Scheduling automated regular updates for all IoT devices, the Raspberry Pi, and the cloud platform to apply the latest security patches. |
| Network Monitoring and Intrusion Detection | Implementing systems that monitor network traffic and analyze it for suspicious or unusual activity. | Detecting and responding to potential threats in real time, helping to prevent security breaches and data theft. | Implementing a Network Intrusion Detection System (NIDS) to monitor network traffic and send alerts when suspicious patterns are detected. |
| Data Encryption | Encrypting data both while at rest (stored on devices) and during transmission (in transit). | Protecting sensitive data from unauthorized access and ensuring data confidentiality and privacy, even if a device is compromised. | Encrypting the data stored locally on the IoT devices, and using TLS for all data transfer, providing end-to-end encryption. |
| Security Audits and Assessments | Regularly reviewing security configurations and conducting vulnerability assessments. | Identifying and proactively addressing potential security weaknesses within the system, reducing the risk of exploits. | Conducting periodic vulnerability assessments and penetration testing to identify security weaknesses and improve security posture. |
| Physical Security | Securing devices from any form of physical tampering and controlling all forms of unauthorized access. | Protecting the physical hardware from being compromised, preventing unauthorized modification or data extraction. | Ensuring devices are installed in secure physical locations that limit unauthorized access and protect them from tampering. |
| Incident Response Plan | Creating a comprehensive plan to manage and respond to any security breaches or incidents. | Quickly addressing and mitigating the impact of any security incidents, minimizing damage and ensuring business continuity. | Developing a detailed incident response plan with clear steps for containment, eradication, and recovery in case of a security incident. |
For more detailed insights and best practices for securing IoT environments, you can explore the resources provided by organizations such as the OWASP (Open Web Application Security Project) and NIST (National Institute of Standards and Technology). These resources provide in-depth guides and a wealth of information, allowing you to implement the best methods for securing your projects.
For additional information, please visit the NIST Website: NIST Website
- Avoid Movierulzcom Watch Kannada Movies Legally In 2024
- Rulz Movies Kannada 2025 Your Guide To Sandalwoods Best