In an age of ubiquitous connectivity, is your data truly safe? The reality is stark: protecting your Internet of Things (IoT) devices is no longer a matter of choiceit's an imperative. Securing your network necessitates a proactive approach, and implementing a Virtual Private Cloud (VPC) using a Raspberry Pi emerges as a highly effective, accessible, and surprisingly powerful strategy.
As technology continues its relentless integration into the very fabric of our lives, the proliferation of IoT devices across diverse sectors is undeniable. From smart homes and industrial automation to healthcare and transportation, the expansion of connected devices is reshaping industries and everyday experiences. This surge in connectivity, however, simultaneously expands the attack surface, creating new vulnerabilities that demand immediate attention. Organizations and individuals alike must prioritize network security to safeguard against a myriad of potential threats. The humble Raspberry Pi, with its versatility and affordability, presents a compelling solution for establishing a secure and robust VPC environment.
This guide serves as a deep dive into the intricate process of securely connecting remote IoT VPCs using the Raspberry Pi, offering a comprehensive understanding of the underlying principles and practical steps. It provides details on essential tools and software freely available to Windows users, ensuring accessibility for a broad audience. By the end of this exploration, you will be well-equipped with the knowledge to build, manage, and maintain a secure IoT network, thereby ensuring that your valuable data remains shielded from unauthorized access and the ever-present threat of malicious attacks.
- Movierulz Kannada 2025 Your Guide To New Movies Trends
- 5movierulz Kannada Movies In 2025 Risks Safe Alternatives
The Internet of Things (IoT) represents the sprawling and ever-expanding network of physical devices from vehicles and appliances to industrial machinery and countless other objects all equipped with sensors, software, and embedded connectivity, meticulously designed to exchange data in real-time. These interconnected devices are not just automating tasks; they are revolutionizing industries, paving the way for smarter, more efficient operations, and creating entirely new possibilities across a spectrum of human endeavor. However, with this increased connectivity comes an inherent and escalating risk: the risk of security breaches. To mitigate these inherent risks and safeguard against the potential for data theft, disruption, and reputational damage, the deployment of secure solutions, such as a Virtual Private Cloud (VPC), is no longer optional; it is a critical necessity.
According to a report by the globally recognized technology research and advisory firm Gartner, the sheer number of IoT devices deployed worldwide is projected to surge past a staggering 25 billion by the year 2030. This dramatic and exponential growth underscores the critical and urgent importance of securing these devices effectively. Failing to do so could expose sensitive information to the public, disrupt critical operations, and result in significant financial and reputational harm, potentially impacting individuals, organizations, and even entire industries. The scale of this projected expansion only amplifies the risks associated with vulnerable IoT deployments.
IoT devices are often uniquely vulnerable to cyberattacks due to a combination of factors: their widespread and often decentralized deployment, the frequent lack of robust, built-in security measures, and the tendency for devices to be deployed and then "forgotten," leading to outdated firmware and software that are easily exploited. A single compromised device can serve as a dangerous gateway, potentially exposing an entire network to a variety of sophisticated threats. By securely connecting your IoT devices through a well-configured VPC, you can create a vital buffer against these risks and achieve several key security and operational benefits:
- Protect sensitive data from unauthorized access. This foundational measure ensures that confidential information, the lifeblood of many operations, remains private and inaccessible to those without explicit permission.
- Ensure seamless and secure communication between devices. This is critical for facilitating efficient data exchange, enabling real-time monitoring, and improving operational effectiveness.
- Reduce the risk of cyberattacks and data breaches. By strategically limiting access to your network and proactively monitoring traffic for unusual activity, you can significantly decrease the likelihood of successful security incidents and limit the potential impact of any breaches that may occur.
- Enhance overall network performance and reliability. A well-configured VPC, designed with optimization in mind, can improve traffic flow, minimize latency, and ensure that your IoT devices remain responsive and reliable, even under heavy network loads.
A Virtual Private Cloud (VPC) is, at its core, a private and isolated network environment operating within a public cloud infrastructure. This allows users to establish and control isolated sections of the cloud, where they can launch and manage computing resources within a virtual network that they define. A VPC empowers you with granular control over your network infrastructure, granting you authority over the IP address ranges, the creation of subnets, the configuration of route tables, and the deployment of network gateways. This level of control ensures a secure and highly-customized environment perfectly suited to host and manage your IoT devices.
VPCs are particularly advantageous for IoT deployments precisely because they provide an additional and critical layer of security by isolating your devices from the vast and often perilous public internet. This isolation functions as a critical first line of defense, preventing unauthorized access attempts and ensuring that only those devices explicitly authorized to communicate within the network are permitted to do so. This architecture also greatly aids in preventing the spread of malware and minimizes the potential impact of any successful security breach, effectively containing the damage.
The benefits of utilizing a VPC for your IoT infrastructure are numerous and compelling, offering a significant advantage in terms of security, performance, and scalability:
- Enhanced security through network isolation, acting as a crucial first line of defense against external threats.
- Flexible configuration options for subnets and routing, allowing for highly customized network management and optimized resource allocation.
- Improved performance by actively reducing latency and mitigating network congestion, resulting in faster data transfer speeds and more responsive communication between devices.
- Scalability to accommodate the constantly growing and evolving nature of IoT deployments, making your network adaptable to future expansion and evolving needs.
The Raspberry Pi stands out as an exceptional and remarkably versatile tool for a wide range of IoT projects. This compact, affordable, and surprisingly powerful single-board computer has earned immense popularity among hobbyists, educators, and professionals alike. Its versatility and ease of use, combined with its low cost, make it an ideal platform for a wide variety of IoT endeavors, including the crucial task of setting up a secure and resilient VPC environment.
The Raspberry Pi boasts several key features that render it exceptionally well-suited for the demands of IoT projects:
- Compact size and extremely low power consumption, making it ideal for deployment in various settings, even those with limited space or power availability.
- Support for multiple operating systems, including versatile Linux-based distributions such as Raspberry Pi OS (formerly Raspbian), which offer a wide range of software compatibility and ease of customization.
- Extensive and active community support, coupled with readily available resources, including comprehensive documentation, tutorials, and highly active online forums, ensuring that help is always within reach.
- Compatibility with a vast and ever-expanding range of sensors and peripherals, allowing for seamless integration with other devices and systems, unlocking a world of possibilities for data collection and control.
By strategically leveraging the capabilities of a Raspberry Pi, you can create a secure and highly efficient IoT VPC environment that meticulously meets your specific requirements. This approach offers a powerful combination of security, flexibility, and affordability, empowering you to effectively manage your IoT devices while maintaining a robust security posture.
The process of setting up a secure IoT VPC with a Raspberry Pi involves a series of key steps, each designed to contribute to the overall security and efficiency of your network.
Before you initiate your IoT VPC setup, it's essential to ensure that you have gathered and prepared the following essential components:
- A Raspberry Pi (preferably a Raspberry Pi 4 or later). Newer models offer significantly enhanced processing power, faster network capabilities (including Gigabit Ethernet and improved Wi-Fi), and generally superior overall performance.
- A microSD card with a compatible operating system installed (e.g., Raspberry Pi OS). The operating system serves as the foundational platform upon which your entire VPC will be built. Choose a reliable and well-maintained OS for optimal results.
- A stable and reliable internet connection. Dependable and consistent internet connectivity is absolutely crucial for enabling remote access, facilitating seamless communication, and ensuring that your IoT devices can connect to your VPC.
- A VPC-compatible software solution (e.g., OpenVPN). This software will handle the critical tasks of encrypting your network traffic and securely tunneling all communications, providing a vital layer of security.
Once you have meticulously gathered all of these essential components, follow these methodical steps to configure your Raspberry Pi:
- Insert the microSD card containing your chosen operating system into the Raspberry Pi and power it on.
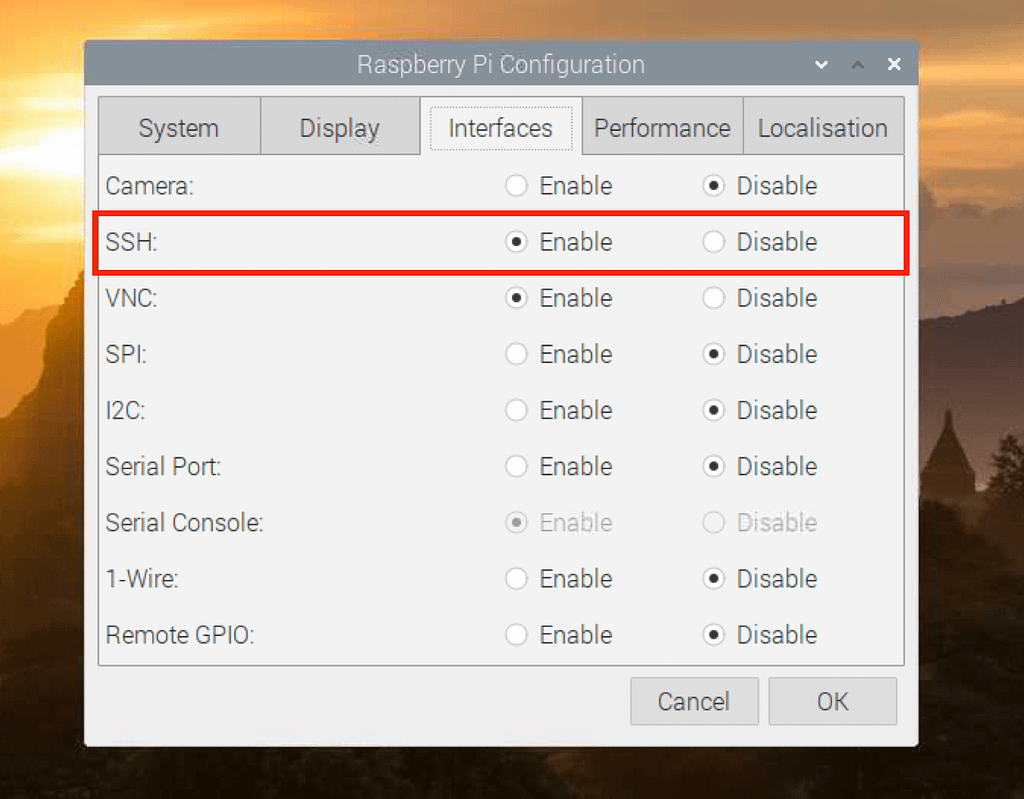
- Establish a connection to your Wi-Fi network or, preferably, connect the Raspberry Pi directly to your network using an Ethernet cable. This step is vital for establishing network connectivity, providing remote access, and enabling your device to communicate.
- Update the operating system to the most recent and secure version using the terminal command:
sudo apt update && sudo apt upgrade. This command ensures that you possess the latest security patches and software updates, significantly enhancing your network's security posture. - Install the required software necessary for successfully setting up and configuring your VPC (e.g., OpenVPN), following the provided instructions carefully.
OpenVPN has emerged as a highly popular and widely trusted open-source software solution for creating secure virtual private networks. Its reliability, ease of use, and robust security features have made it a preferred choice for individuals and organizations alike. OpenVPN allows you to effortlessly establish secure, encrypted tunnels, safeguarding your network traffic from prying eyes. It's fully compatible with the Windows operating system and can be seamlessly integrated with a Raspberry Pi to create a secure and resilient IoT VPC environment. This powerful combination offers a robust, cost-effective, and readily accessible solution for securing all of your network traffic, protecting sensitive data from interception and malicious attacks.
To download OpenVPN for Windows, simply visit the official OpenVPN website: https://openvpn.net/community-downloads/. Once you have reached the website, carefully follow the provided installation instructions, paying close attention to each step to ensure a smooth and successful setup process. This will equip you with the necessary tools and components to create secure and encrypted connections between your devices. The official website is the best place to obtain the software, ensuring that you are receiving the latest version and a secure download.
While OpenVPN is undeniably a powerful and highly recommended choice, several alternative tools also exist, each bringing its own unique strengths and advantages to the table, allowing you to choose the solution best suited for your specific needs and requirements:
- Tailscale: A user-friendly and streamlined solution for effortlessly creating secure networks across multiple devices. Tailscale simplifies the setup process and offers a more intuitive user experience.
- WireGuard: A modern and lightweight VPN solution, WireGuard is renowned for its exceptional performance, enhanced security features, and its ability to provide a more streamlined and efficient VPN experience.
- ZeroTier: A cloud-based networking platform that simplifies the creation and management of IoT VPCs, particularly well-suited for larger and more complex deployments. This platform provides a user-friendly interface and automated configuration, simplifying network administration.
Implementing robust and well-considered security practices is absolutely vital to ensure the continued integrity and secure operation of your IoT VPC. Below are some of the most critical and essential best practices to consider when deploying and maintaining your secure network:
Implementing strong and robust authentication methods, such as two-factor authentication (2FA), can significantly bolster the overall security posture of your IoT VPC. 2FA ensures that only authorized users, possessing both something they know (like a password) and something they have (like a code from a mobile device), are granted access to the network and its valuable resources. This approach is highly effective in preventing unauthorized access attempts, even if an attacker has managed to compromise a user's password.
Keeping your software and firmware meticulously up to date is an indispensable practice for maintaining a secure and protected environment. Regular software updates and firmware patches often contain crucial security patches that are designed to address newly discovered vulnerabilities. These vulnerabilities, if left unaddressed, could be exploited by malicious actors, putting your network at risk. Proactive updates are essential for strengthening your network's defenses.
Regularly and systematically monitoring your network activity is critical for detecting and preventing unauthorized access attempts and identifying suspicious or malicious behavior. Employing network monitoring tools, such as Wireshark and Snort, allows you to analyze network traffic in detail, identify unusual or suspicious patterns, and proactively identify potential threats before they can cause significant damage. These tools can provide valuable insights into your network's activity.
Several common challenges can often arise during the setup and the ongoing operation of an IoT VPC. Fortunately, readily available and well-established solutions exist to effectively address these potential issues:
Challenge: High Latency and Slow Data Transfer Speeds
Solution: Optimize your network settings to prioritize critical and essential traffic and to significantly reduce latency. This involves configuring Quality of Service (QoS) settings, which prioritize specific types of traffic, and strategically adjusting your network bandwidth allocation, ensuring that essential data transfers are prioritized, especially when bandwidth is limited or congested.
Challenge: Compatibility Issues Between Devices and VPC Software
Solution: Meticulously ensure that all IoT devices are fully compatible with your chosen VPC solution and that you consistently use standardized communication protocols. This requires verifying that all devices connected to the VPC fully support the VPN protocols selected for use. Whenever possible, consider employing standardized communication protocols such as MQTT or CoAP, as this enhances compatibility and simplifies interoperability between devices, making your network more robust and reliable.
Securing your IoT devices through the use of a Virtual Private Cloud (VPC) implemented with a Raspberry Pi is a powerful and remarkably cost-effective solution for protecting your valuable network and the sensitive data it carries. This approach offers a compelling and practical combination of robust security, unparalleled flexibility, and, critically, affordability, making it accessible to both hobbyists and experienced professionals alike.
By meticulously following the comprehensive steps and utilizing the information and guidance provided throughout this guide, you can establish a secure and highly efficient IoT VPC environment that caters precisely to your specific needs and requirements. Remember to consistently and proactively implement the outlined best practices and to promptly update your software and firmware to maintain a robust and resilient security posture. This diligence will ensure the long-term safety and security of your valuable data and all of your connected devices, protecting your investment and ensuring peace of mind.
This project has the potential to be exceedingly useful to a broad spectrum of individuals and organizations. To successfully initiate this project, you can follow these recommended steps:
1. Confirm that you possess all the necessary hardware, including the Raspberry Pi itself, a reliable microSD card for storing the operating system, and a suitable charger to power the device.
2. Download and install the necessary software required for setting up and configuring your VPC, such as OpenVPN or the alternative solution that best fits your needs.
3. Carefully follow the detailed steps provided to create and effectively manage your secure IoT network, meticulously protecting your valuable data from unauthorized access and potential threats.
4. Make every effort to fully comprehend all of the information and guidance presented within this article, paying close attention to the technical details and practical instructions.
5. Exercise caution and attention to detail when implementing and building this type of project, paying careful attention to each step and making sure that you fully understand the implications of each configuration choice.
6. Stay connected with the ongoing series of articles and resources provided here, as well as other reputable sources, to continuously expand your knowledge and understanding of this critical and evolving field.
- Luke Combs Democrat Or Not Decoding His Political Views
- Remote Iot Batch Jobs Revolutionizing Industries Beyond