Are you looking to break free from the confines of your physical location and take complete control of your Internet of Things (IoT) devices, no matter where you are? Building a RemoteIoT system with Virtual Private Cloud (VPC) SSH and a Raspberry Pi offers a potent blend of accessibility, security, and efficiency, transforming the way you interact with your connected devices.
In a world increasingly defined by seamless connectivity, the ability to manage and monitor devices from any corner of the globe has become not just a convenience, but a necessity. This guide serves as your comprehensive roadmap, detailing the practical steps required to establish a robust and secure remote IoT infrastructure. We will explore the essential components: RemoteIoT solutions, the power of VPC SSH, the versatility of the Raspberry Pi, and the indispensable role of free Windows utilities. This article will dissect the complexities of setting up a secure network, offering clear, concise instructions that cater to both beginners and seasoned tech enthusiasts alike. The ultimate aim is to equip you with the knowledge and skills necessary to create a resilient and reliable remote IoT environment capable of handling the demands of the modern digital age. This detailed exploration encompasses every facet of the process, from initial setup considerations to the troubleshooting of common issues, ensuring a smooth and successful implementation journey.
This setup empowers you to access and manage your devices securely, no matter your physical location. This article will explore the tools and techniques required to achieve this goal, including a focus on readily available, free Windows utilities.
- Remote Iot Platforms A Comprehensive Guide Tutorial
- 5movierulz Kannada 2024 Exploring Amp Legal Movie Alternatives
By the time you finish reading this guide, you will have a solid understanding of how to configure RemoteIoT, set up VPC SSH, and optimize your Raspberry Pi for remote access, allowing you to build a truly connected and controllable ecosystem.
| Topic | Details |
|---|---|
| RemoteIoT | Enables users to remotely manage IoT devices, offering a suite of features including device monitoring, configuration management, and comprehensive data visualization. |
| VPC SSH | Provides secure and encrypted connections to your devices, an essential element in protecting sensitive data transmitted over the network. Furthermore, VPC SSH offers scalability, allowing your network to expand and adapt to your evolving IoT needs. |
| Raspberry Pi | A cost-effective and highly flexible single-board computer, ideally suited for a variety of IoT projects. It boasts low power consumption, compatibility with a multitude of operating systems, and the ability to connect to a wide range of peripherals, making it a versatile platform for remote device management. |
| Free Windows Tools | These tools significantly enhance the RemoteIoT experience. Key examples include PuTTY (an SSH client), WinSCP (a secure file transfer utility), and Visual Studio Code (a sophisticated code editor with dedicated support for IoT development). |
For more in-depth information about the Raspberry Pi and its capabilities, we recommend visiting the official Raspberry Pi Foundation website.
The following sections will systematically detail the required steps, from the selection of a suitable cloud provider to the implementation of vital security measures designed to safeguard your devices and data.
- Remote Iot Batch Jobs On Aws Examples Best Practices
- 7movierulz 2024 Download Kannada Risks Safe Alternatives
RemoteIoT is a powerful solution, providing users with the ability to remotely manage their IoT devices. By integrating it with VPC SSH, you can establish a secure and scalable network, capable of meeting both current and future demands. The integration of the Raspberry Pi further enhances this setup, delivering a cost-effective and flexible hardware platform that can be readily adapted to a variety of use cases.
Why Choose VPC SSH?
Virtual Private Cloud (VPC) SSH offers a compelling set of advantages for the remote management of your IoT devices:
- Enhanced Security: Protect your data transmissions with robust, end-to-end encrypted connections, mitigating the risks associated with unauthorized access and data breaches.
- Scalability: Effortlessly expand your network as your IoT ecosystem grows, allowing you to add more devices and accommodate increasing demands without compromising performance or security.
- Cost-Effective: Leverage the power of cloud services without incurring prohibitive costs, enabling you to build and manage your remote IoT infrastructure efficiently and affordably.
Incorporating these technologies into your workflow can significantly enhance both the efficiency and reliability of your remote device management operations.
The Raspberry Pi has rapidly become a favorite amongst hobbyists, tech enthusiasts, and professionals alike. Its small form factor, affordable price point, and extreme flexibility make it an ideal choice for IoT projects.
Key Features of Raspberry Pi
- Low power consumption, extending battery life in portable applications and reducing overall energy costs.
- Support for multiple operating systems, allowing you to choose the environment that best suits your specific needs.
- Compatibility with a wide range of peripherals, providing virtually limitless possibilities for customization and expansion.
When combined with RemoteIoT and VPC SSH, the Raspberry Pi becomes a powerful tool for managing your devices remotely, offering a blend of functionality, affordability, and ease of use that is hard to beat.
Creating a VPC is a fundamental step in establishing a secure remote network. To successfully set up your VPC, carefully follow these steps:
Step-by-Step Guide to VPC Creation
Choose a cloud provider that offers robust VPC capabilities. Popular options include Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure. Consider factors such as pricing, features, and geographical availability when making your selection.
Create a new VPC within your chosen cloud provider's console. Define the IP address range (CIDR block) for your VPC. This range should be private and not overlap with any other networks your devices might be connected to. Carefully plan your address space to accommodate the future growth of your network.
Set up subnets within your VPC. Subnets are logical divisions of your VPC's IP address range. Configure routing tables to direct network traffic within your VPC and to the internet (if required). Consider using public and private subnets to enhance security and manage access control.
Enable SSH access to your Raspberry Pi by configuring security groups. Security groups act as virtual firewalls, controlling inbound and outbound traffic to your instances. Define rules to allow SSH traffic (typically on port 22) from your trusted IP addresses or network ranges. Carefully consider your security group rules to minimize the attack surface of your devices.
By meticulously following these steps, you can create a secure and fully functional VPC, providing a foundation for the reliable and secure remote management of your IoT devices.
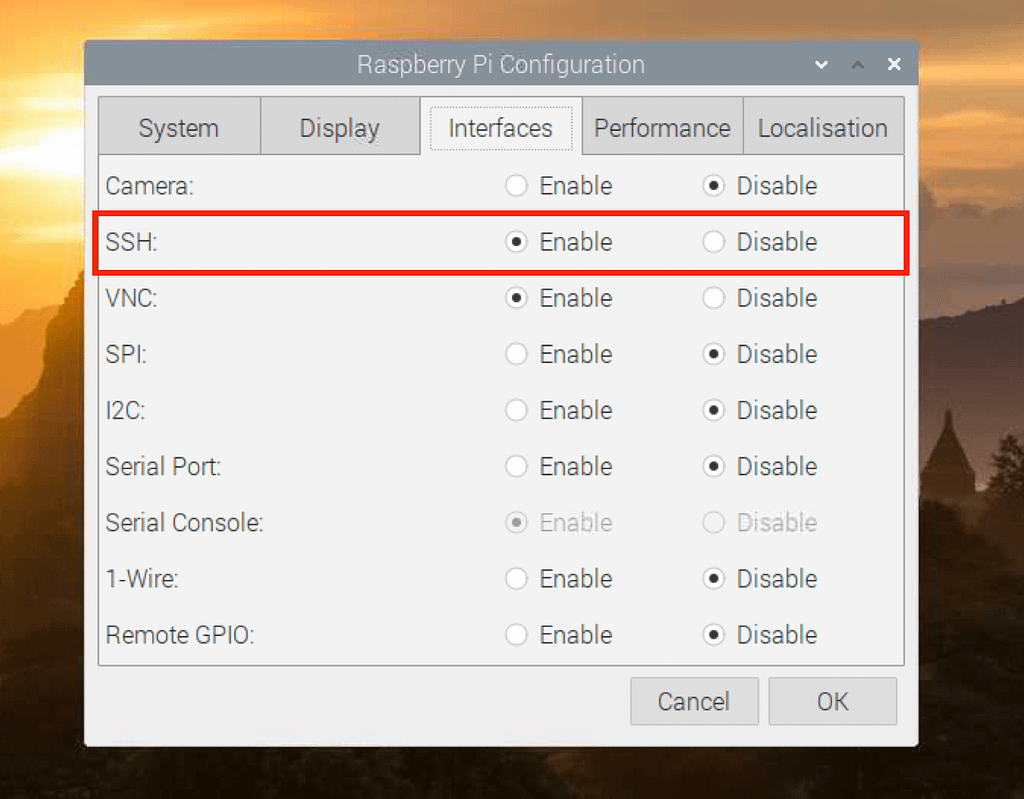
SSH (Secure Shell) is a vital protocol that enables secure remote access to your Raspberry Pi. Enabling SSH access is straightforward, and here's how:
Enabling SSH on Your Raspberry Pi
Connect your Raspberry Pi to a monitor and keyboard, or access it via an existing SSH connection. This initial configuration often requires direct access to the device.
Open the terminal on your Raspberry Pi, either directly or through the existing SSH connection. Then, type the following command:
sudo raspi-config. This command will launch the Raspberry Pi configuration tool.Navigate to the "Interfacing Options" menu using the arrow keys and select it. From there, locate and enable SSH. This step allows external connections to be established with your Raspberry Pi through the secure SSH protocol.
Reboot your Raspberry Pi to apply the changes. This reboot process activates the SSH service, allowing remote connections to be established. After the reboot, you should be able to connect remotely.
Once SSH is successfully enabled, you will be able to access your Raspberry Pi remotely from any device on the same network, as well as from external locations, provided you have configured your VPC and firewalls accordingly.
RemoteIoT solutions offer a suite of powerful tools that significantly simplify the management of your IoT devices. These tools are essential for a streamlined and efficient remote management experience:
Popular RemoteIoT Tools Key Components
- Device monitoring software: For real-time insights into the performance and health of your devices. This includes monitoring CPU usage, memory, network traffic, and other critical metrics.
- Configuration management tools: To remotely configure and manage your device settings, including software updates, network configurations, and security parameters.
- Data visualization platforms: For the ability to analyze the data streams gathered from your devices. These platforms can allow you to track trends, identify anomalies, and make data-driven decisions.
By leveraging these tools, you can gain a higher degree of control over your IoT ecosystem.
There are numerous free Windows tools that dramatically improve the RemoteIoT experience. These freely available resources, when coupled with the functionality of the Raspberry Pi and VPC SSH, provide a robust and versatile toolkit. Key examples include:
Recommended Windows Tools
- PuTTY: A free and highly popular SSH client for Windows. It allows you to securely connect to your Raspberry Pi via SSH, providing a command-line interface for remote control and management. PuTTY is known for its stability, its extensive configuration options, and its wide range of terminal emulations.
- WinSCP: A secure file transfer program that uses the SSH protocol. WinSCP facilitates the secure transfer of files between your Windows computer and your Raspberry Pi. It offers a user-friendly interface, supporting features like drag-and-drop file transfer, directory synchronization, and a built-in text editor.
- Visual Studio Code: A versatile and powerful code editor, also with dedicated extensions that add direct support for IoT development. VS Code provides a wide array of features, including syntax highlighting, code completion, debugging support, and integrated terminal access, making it an excellent choice for developing and deploying code to your Raspberry Pi.
These tools can be downloaded from their official websites, ensuring that you always have access to the most up-to-date and secure versions. Regularly updating these tools is also essential for maintaining the security of your system.
Even with a perfectly configured setup, unforeseen issues can arise. Preparing for these potential challenges and knowing how to address them is a key aspect of successfully implementing a remote IoT network:
Common Problems and Solutions
- Ensure SSH is enabled on your Raspberry Pi: Confirm SSH is activated in the Raspberry Pi configuration (raspi-config). Verify that the SSH service is running using the command
sudo service ssh statusand if the SSH service is not running, you can start the service withsudo service ssh start. - Check your network settings and firewall rules: Verify that your Raspberry Pi has a valid IP address and is able to access the network. Confirm that your firewall rules are correctly configured to allow SSH traffic (typically on port 22) from your trusted source IP addresses or network ranges. Also, ensure there are no network restrictions on your Raspberry Pi itself.
- Verify the IP address and port number: Ensure that you are connecting to the correct IP address and that the port number is specified (typically port 22 for SSH). Use the
ifconfigcommand on your Raspberry Pi to determine its current IP address. Also, make sure your VPC configuration allows SSH traffic and that you can ping the Raspberry Pi from your remote location.
By having a systematic approach to these common troubleshooting issues, you can effectively diagnose and resolve connectivity problems.
Security should be a paramount concern when setting up any remote IoT network. Robust security practices are vital to protecting your devices and data from unauthorized access and potential threats:
Key Security Measures for a Robust System
- Use strong, unique passwords for all devices: Implement complex passwords for your Raspberry Pi, your cloud accounts, and any other services involved. Avoid using easily guessable passwords and make sure that each password is unique. Consider using a password manager to generate and store your credentials securely.
- Enable two-factor authentication (2FA) wherever possible: This significantly enhances security. 2FA requires a second verification factor, such as a code from an authenticator app or a one-time password (OTP) sent to your phone, in addition to your password. This measure adds an extra layer of protection and makes unauthorized access far more difficult.
- Regularly update your software and firmware: Keep your Raspberry Pi's operating system, all installed software packages, and the firmware of your devices up-to-date. These updates frequently include security patches that address known vulnerabilities, making it harder for attackers to exploit your system. Consider enabling automatic updates where appropriate.
By implementing these essential security measures, you can significantly reduce the risk of unauthorized access and protect your valuable data.
To ensure optimal performance of your RemoteIoT setup and to maintain a reliable and efficient system, consider these advanced optimization strategies:
Optimization Strategies for Enhanced Performance
- Minimize unnecessary services running on your Raspberry Pi: Identify and disable any services that are not required for your remote access and device management tasks. This reduces the system load, frees up resources, and improves the overall responsiveness of your Raspberry Pi. Regularly audit the services running on your device and remove any unnecessary components.
- Use compression techniques to reduce data transfer overhead: Implement data compression (e.g., gzip, bzip2) when transferring files or transmitting data over the network. This reduces the amount of data that needs to be transmitted, which can significantly speed up the transfer times, especially when operating on slower networks.
- Monitor network traffic and adjust settings as needed: Continuously monitor your network traffic using tools like
iftoporvnstaton your Raspberry Pi. Analyze the traffic patterns to identify any bottlenecks or excessive bandwidth usage. Adjust the network settings, optimize configurations, or upgrade your network infrastructure accordingly to improve performance and reliability.
- Free Iot Device Management Your Guide To Software Solutions
- Movierulz Kannada 2024 Updates Risks Legal Alternatives