Can you truly unlock the full potential of your Raspberry Pi from anywhere, anytime, without spending a dime? The answer is a resounding yes, and mastering remote SSH access from your Mac, even when navigating the complexities of a NAT router, is the key.
The proliferation of Raspberry Pi devices in personal projects, home automation setups, and remote server management has made the ability to remotely access them a highly sought-after skill. However, the intricacies of Network Address Translation (NAT) and the sometimes-daunting task of configuring network settings often present significant hurdles. This guide provides a clear, step-by-step approach to configuring remote SSH access, empowering you to securely connect to your Raspberry Pi from your Mac without incurring any financial burden.
By the end of this piece, you'll possess a solid understanding of SSH configuration on your Raspberry Pi, the process of setting up port forwarding on your router, and how to leverage tools like ngrok or localtunnel to gracefully bypass NAT restrictions. Prepare to elevate your tech prowess lets delve into the practicalities of this essential skill!
- Hdhub4u Hub Is It Safe Legal A Streaming Guide
- Kannada Movierulz Piracy Risks Alternatives What You Need To Know
| Feature | Details |
|---|---|
| Purpose of Remote SSH | Enables secure and efficient connectivity to a Raspberry Pi from a Mac, allowing control from anywhere in the world. |
| Key Advantages | Encryption of all data, authentication mechanisms, and compatibility with macOS. |
| Cost Consideration | Focus on free tools and methods to achieve remote access without any expenses. |
| Essential Tools | SSH Client (built-in to macOS), Router with Port Forwarding capabilities or tools like ngrok/localtunnel. |
| Benefits of Free Remote Access | Avoid subscription fees, maintain control, and build technical skills. |
SSH, or Secure Shell, is more than just a tool; its a fundamental protocol for secure network communication. It acts as a cryptographic bridge, enabling secure interaction between devices across potentially hostile, unsecured networks. For those with a Raspberry Pi, mastering SSH means gaining complete control from afar. This is particularly critical when the Pi resides behind a NAT router a common scenario that adds a layer of complexity, yet is readily overcome.
At its core, SSH works by encrypting all the data exchanged between two points. This ensures that even if an unauthorized party intercepts the communication, the data remains unreadable. Furthermore, SSH leverages robust authentication protocols to ensure that only authorized users gain access. Its a security-first approach, built to protect your data and your device.
Let's break down some core terms to solidify your understanding:
- Ssis641 Your Guide To Data Integration Transformation
- Hdhub4u South Hindi Dubbed Your Guide To Hindidubbed Movies
- Client: In this context, it's the device youre using to connect to your Raspberry Pi. This is typically your Mac.
- Server: The Raspberry Pi itself, acting as the remote server, awaiting commands and information.
- Port: This is a virtual doorway for communication. The default SSH port is 22, but for enhanced security, it's often best to change it.
The process involves establishing a secure channel, encrypting all data transferred between the client (your Mac) and the server (your Raspberry Pi). The use of public-key cryptography is a cornerstone of this security, authenticating users and ensuring the integrity of communication. A firm grasp of these basics prepares you to troubleshoot issues that may arise and to optimize your setup for peak performance.
Before establishing remote access, you have to prepare your Raspberry Pi for the journey. This involves a few key configuration steps to ensure it's ready to accept remote SSH connections. The following steps are designed to be straightforward and easy to follow.
Enabling SSH on the Raspberry Pi
SSH, by default, is disabled on Raspberry Pi OS. You must enable it before you can remotely access your Pi. Follow these steps:
- Power Up and Connect: Start by powering on your Raspberry Pi and connecting it to your local network, typically via Ethernet or Wi-Fi.
- Access the Configuration: Open a terminal on your Pi (or access it via a connected monitor and keyboard) and type the command
sudo raspi-config. This is your gateway to system-level settings. - Navigate to Interfacing Options: Use the arrow keys to move through the menu. Go to Interfacing Options and select it.
- Enable SSH: Within the Interfacing Options, find and select "SSH". You will be prompted to enable it. Choose "Yes".
- Reboot for Changes: After enabling SSH, the system will likely prompt you to reboot your Raspberry Pi. Allow this to complete.
Pinpointing Your Raspberry Pis Address
With SSH enabled, the next vital piece of information is your Raspberry Pi's IP address. This address is how you'll identify your Pi on the network. Use the following command in the terminal to find it:
ifconfig
The output can be a bit dense, so look for the inet address under either the wlan0 section (if using Wi-Fi) or the eth0 section (if using Ethernet). This is your Raspberry Pis local IP address, and it's crucial for connecting.
Now that your Raspberry Pi is configured, it's time to switch gears and prepare your Mac to connect to it. This involves using the built-in SSH client on macOS and setting up SSH keys for added security.
The macOS operating system boasts a powerful SSH client built directly into the Terminal application. There's no need to install any additional software to begin your remote access journey.
Initiating the Connection
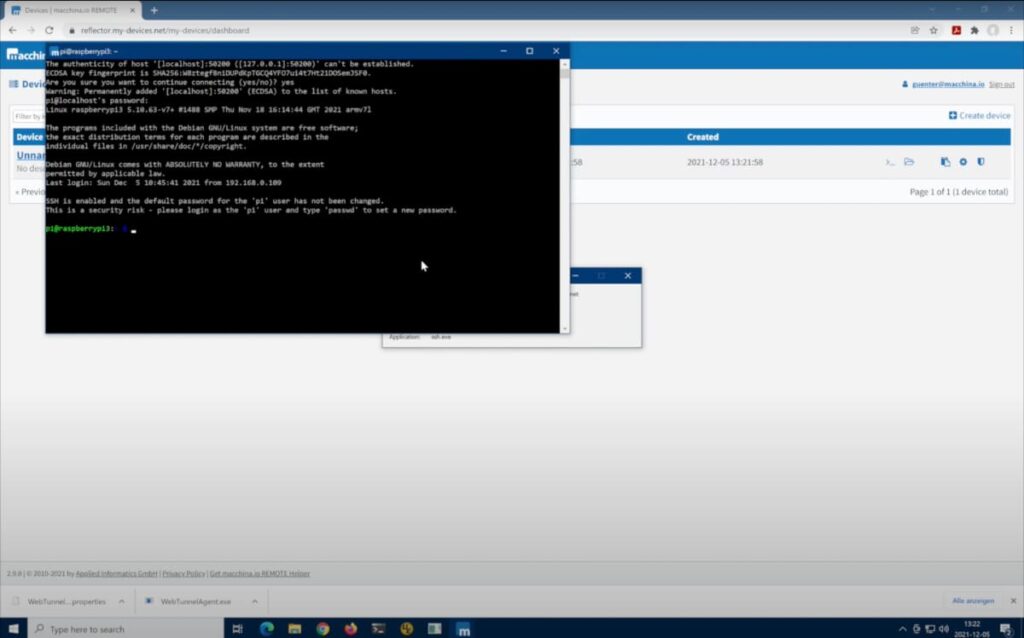
To connect to your Raspberry Pi, open the Terminal app on your Mac. You will then use the following command, replacing "your-raspberry-pi-ip-address" with the actual IP address you noted earlier:
ssh pi@your-raspberry-pi-ip-address
For example, if your Raspberry Pi's IP address is 192.168.1.100, the command would look like this: ssh pi@192.168.1.100. You will be prompted to enter the password for the "pi" user (the default username on Raspberry Pi OS). Enter the password and press enter. If everything is set up correctly, you should now be connected to your Raspberry Pi's command-line interface.
Leveling Up Security with SSH Keys
While passwords work, SSH keys provide a significantly enhanced security layer. Instead of typing your password every time, SSH keys enable password-less login. Lets generate an SSH key pair on your Mac.
- Generate the Key Pair: Open the Terminal on your Mac and run the command:
ssh-keygen -t rsa -b 4096
This command creates a new SSH key pair, using the RSA algorithm and a key length of 4096 bits (a strong level of encryption). Youll be asked where to save the key. You can typically accept the default location and press Enter. You may also be prompted to set a passphrase. A passphrase adds another layer of security, but is optional. If you dont set a passphrase, you will be prompted for it every time you use the key.
- Copy the Public Key: Now that you have a key pair, you need to copy the public key to your Raspberry Pi. Use the following command, substituting your Raspberry Pis IP address as before:
ssh-copy-id pi@your-raspberry-pi-ip-address
This command securely copies your public key to the Raspberry Pis `~/.ssh/authorized_keys` file, allowing you to log in without a password. You may be prompted to enter your password one last time to complete the process.
With SSH keys in place, your connections become significantly more secure. If you set a passphrase, you will be prompted to enter it when connecting, adding another layer of security. If you did not set a passphrase, you'll connect without being asked for a password.
Understanding NAT (Network Address Translation) is key to successfully accessing your Raspberry Pi remotely. NAT is the backbone of modern home and business networks, but it can complicate remote access to devices like your Raspberry Pi.
NAT's core function is to allow multiple devices to share a single public IP address. This feature is essential for several reasons:
- IP Address Conservation: With the depletion of IPv4 addresses, NAT allows a single IP address to serve a multitude of devices.
- Enhanced Security: NAT provides a layer of security by hiding the internal network from the outside world.
When your devices on your local network send requests out to the internet, the router rewrites the source IP address of the outgoing traffic, replacing the private IP address of your device with the public IP address of the router. When the responses come back, the router translates the destination IP address to the private IP address of the internal device and forwards the traffic accordingly. However, this translation process can create complications when trying to access internal devices from the outside.
Navigating the Different NAT Types
There are different types of NAT, each with its own characteristics. Understanding the type of NAT used by your router will help you troubleshoot any issues.
- Full Cone NAT: This is the least restrictive type. Any external host can send traffic to an internal host using a specific port, regardless of whether the internal host has previously initiated a connection.
- Restricted Cone NAT: Only external hosts that have received a packet from the internal host can send traffic to the internal host.
- Port-Restricted Cone NAT: Similar to Restricted Cone NAT, but with an added requirement: the external host must use the same source port that the internal host used to communicate.
- Symmetric NAT: This is the most restrictive type of NAT. It maps each connection from an internal host to a unique external IP address and port. This makes it more difficult to set up inbound connections.
The type of NAT you have will affect how you need to set up port forwarding. If you have a more restrictive NAT type, you might need to use tools like ngrok or localtunnel, which are discussed later in this guide.
Port forwarding is the fundamental technique for enabling remote access. This allows you to define specific "virtual doorways" that connect the outside world to your Raspberry Pi. Properly configuring port forwarding is vital for enabling remote SSH into Raspberry Pi behind a NAT router on Mac.
Unlocking Your Router's Settings
The first step involves accessing your routers admin interface. The specific steps vary depending on the make and model of your router, but the process is generally similar:
- Find Your Router's IP Address: Your router's IP address is typically found in your network settings on your Mac, or sometimes printed directly on the router itself. Common default addresses include 192.168.0.1 or 192.168.1.1.
- Access the Admin Interface: Open a web browser and type your router's IP address into the address bar. Press Enter.
- Log In: You will be prompted for a username and password. These are usually printed on the router or provided in the router's documentation. Common default combinations include "admin" and "password", but this varies.
Configuring the Doorways
Once you're logged into your router's admin interface, navigate to the "Port Forwarding" or "NAT" section. Here's how to set up the necessary rules:
- Add a New Rule: Find the option to add a new port forwarding rule. The interface may have different labels, but the objective is the same.
- Populate the Details: You'll need to enter the following information for the SSH service:
- Service Name: You can call this something descriptive, like "SSH" or "Raspberry Pi SSH."
- External Port: This is the port on your router that will receive external traffic and forward it to your Raspberry Pi. The standard SSH port is 22. For added security, you could choose a higher, non-standard port (e.g., 2222).
- Internal IP Address: This is the local IP address of your Raspberry Pi. (Remember the
ifconfigcommand from the Raspberry Pi setup?). - Internal Port: This is the port on your Raspberry Pi that SSH is listening on. Typically, this is also 22.
- Save and Restart: Save your changes, and restart your router if the interface requires it.
If the routers NAT implementation is not conducive to your goals, or if you are behind a particularly restrictive NAT setup, tools like ngrok or localtunnel provide an elegant solution. They are designed to tunnel traffic from the public internet to your local device, bypassing some of the complexities of NAT.
ngrok
ngrok is a popular choice because its easy to set up and use. It establishes a secure tunnel, allowing you to expose your Raspberry Pi to the internet. Here's how to get started:
- Installation: Visit the ngrok website and download the appropriate version for your operating system. For macOS, this will typically be a pre-compiled binary.
- Run ngrok: Open a terminal window. Navigate to the directory where you downloaded the ngrok executable (e.g., the Downloads folder). Then run the command:
./ngrok tcp 22
This tells ngrok to create a TCP tunnel that forwards traffic on port 22 (the default SSH port) to your local device (your Raspberry Pi). You might also need to run `chmod +x ngrok` to make the ngrok executable.
After running this command, ngrok will provide you with a public URL (a TCP address) that you can use to access your Raspberry Pi remotely. This is the address you will use in the ssh command. Be sure to remember the port number provided by ngrok in the URL, as it will likely be different from port 22.
localtunnel
localtunnel offers similar functionality as ngrok. It is a useful tool for quickly creating tunnels. Install it using npm (Node Package Manager):
- Installation: If you don't have Node.js and npm installed, youll need to install Node.js first. Then, install localtunnel globally using the following command in your terminal:
npm install -g localtunnel
- Run localtunnel: Then, run this command in your terminal:
lt --port 22
This command will expose port 22 on your Raspberry Pi to the internet. localtunnel will then provide you with a public URL to connect to your Raspberry Pi remotely.
Securing your remote SSH connection is paramount, and adopting robust security practices is essential to safeguard your Raspberry Pi and any sensitive data it might contain. A few key steps can significantly reduce the risk of unauthorized access.
Hardening Your Fortress
Here are some critical practices you should implement:
- Changing the Default SSH Port: Changing the standard SSH port from 22 to a different, non-standard port is an effective strategy to minimize the risk of automated attacks. Automated bots often scan for services running on default ports. Here's how to change it:
- Edit the SSH Configuration File: Open the SSH configuration file using a text editor:
sudo nano /etc/ssh/sshd_config
- Modify the Port Value: Find the line that says "Port 22" and change "22" to your preferred port number (e.g., 2222 or any port number above 1024 that's not in use). Save the file.
- Restart the SSH Service: Restart the SSH service so that the changes take effect:
sudo service ssh restart or sudo systemctl restart ssh
- Disable Password Authentication: To further enhance security, it's a strong practice to disable password-based authentication altogether. This forces users to use SSH keys, which are far more secure. Follow these steps:
- Edit the SSH Configuration File: Re-open the sshd_config file with your preferred text editor:
sudo nano /etc/ssh/sshd_config
- Set PasswordAuthentication to "no": Find the line that says "PasswordAuthentication yes" and change it to "PasswordAuthentication no". Save the file.
- Restart the SSH Service: Restart the SSH service for the changes to apply:
sudo service ssh restart or sudo systemctl restart ssh
Even with careful configuration, you may encounter problems when trying to connect to your Raspberry Pi remotely. This section addresses common troubleshooting issues and offers straightforward solutions.
Common Hurdles
Here are some typical issues and how to resolve them:
- Connection Refused: If you see the "Connection refused" error, it usually means that the SSH service is not running, or theres a networking issue. Here's what to check:
- SSH Service Status: Ensure the SSH service is running on your Raspberry Pi. Try running
sudo service ssh statusto verify its status. If it's not running, start it withsudo service ssh start. - Port Forwarding Verification: Double-check that port forwarding is correctly configured on your router, ensuring it points to the correct internal IP address and port of your Raspberry Pi.
- Firewall Considerations: Ensure that your firewall is not blocking the SSH port (typically port 22, or the custom port you configured).
- Timeout Errors: Timeout errors usually indicate network connectivity issues, where the connection is initiated, but a response isn't received within the expected time frame. The following should be checked:
- IP Address Verification: Confirm that your Raspberry Pi's IP address hasn't changed.
- Router's Public IP: Check if your routers public IP address is accessible from outside your network. You can do this by trying to access the public IP address from another network.
Remember, remote SSH access provides not just the ability to manage your Raspberry Pi remotely but also the power to learn, experiment, and expand your skillset in the world of technology. Start today, and enjoy the freedom of accessing your projects from anywhere!
- Ssis641 Your Guide To Data Integration Transformation
- Understanding Maal49 Unveiling The Future Of Tech Innovation